Home »
SysAdmin
» Install and Test Comodo Firewall Against BackTrack
Install and Test Comodo Firewall Against BackTrack
| Section 0. Background Information |
- Comodo Firewall
- Comodo Internet Security was designed around the concept of layered security and provides the following layers of protection: Antivirus, Firewall, Host-based intrusion prevent (Defense+), and Remote assistance (GeekBuddy).
- Lab Notes
- In this lab we will do the following:
- Download Comodo Firewall
- Test Comodo Firewall Against BackTrack (Ping)
- Test Comodo Firewall Against BackTrack (nmap basic scan)
- Test Comodo Firewall Against BackTrack (nmap half-open TCP scan)
- Test Comodo Firewall Against BackTrack (nmap SCTP INIT scan)
- Test Comodo Firewall Against BackTrack (nmap intense scan)
- Prerequisites
- Instructions:
- Windows 7: Lesson 1: Installing Windows 7
- BackTrack: Lesson 1: Installing BackTrack 5
| Section 1. Start your Windows 7 VM |
- Edit Virtual Machine Settings
- Instructions:
- Click on Windows 7
- Click on Edit virtual machine
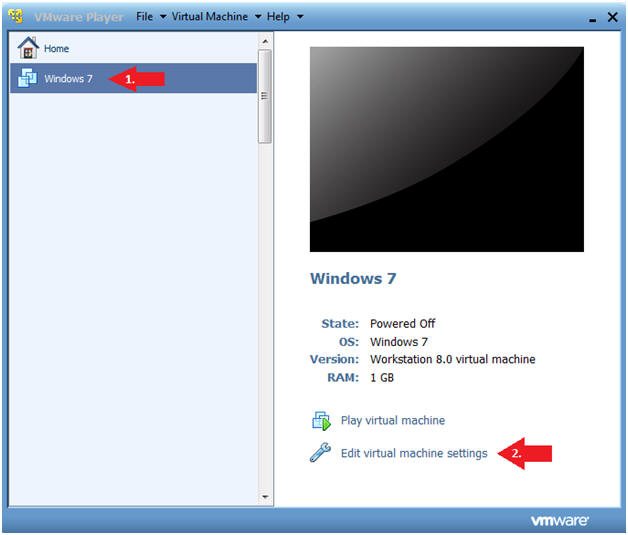
- Configure Network Adapter
- Instructions
- Select Network Adapter
- Click the radio button "Bridged: Connected directly to the physical network."
- Click the Okay button
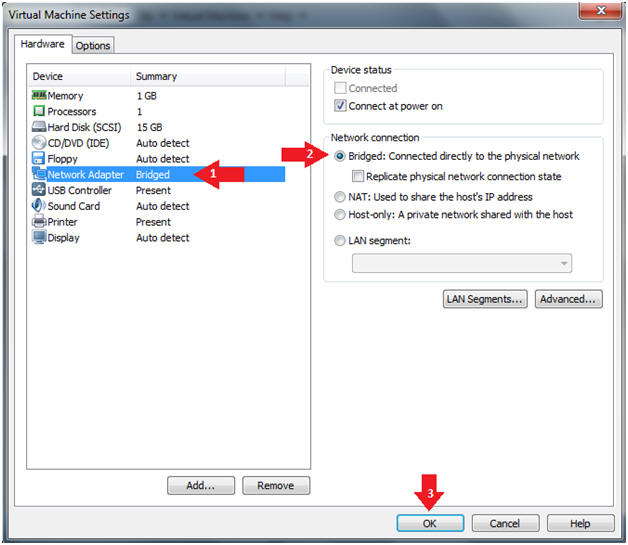
- Start Windows 7
- Instructions:
- Click on Windows 7
- Click on Play virtual machine
| Section 2. Login to Windows 7 |
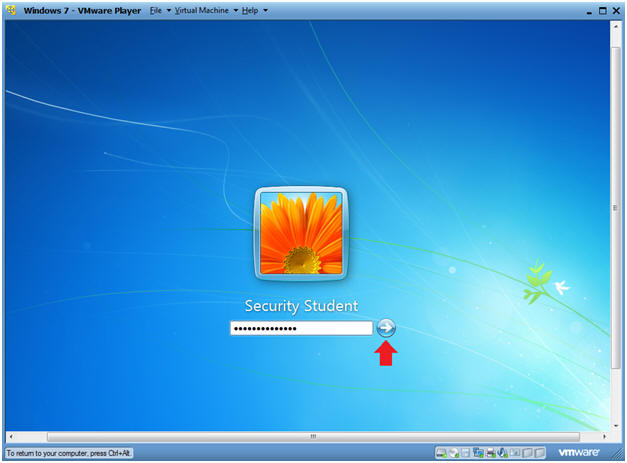
- Login
- Instructions:
- Enter Password
- Click the Blue Arrow
| Section 3. Verify you have a Network IP Address |
- Bring up Command Prompt
- Instructions:
-
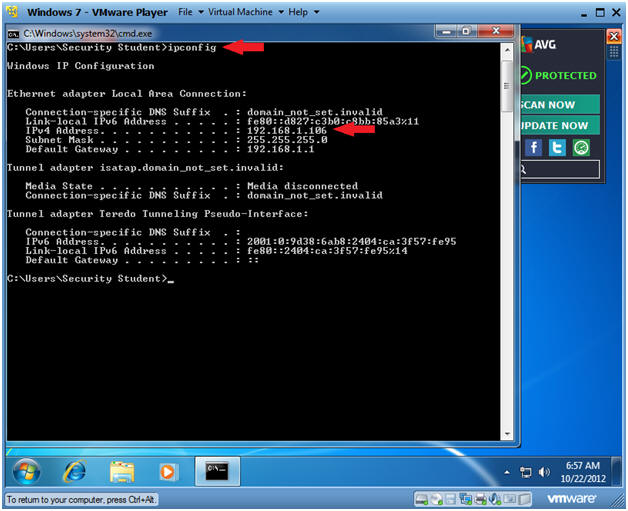
- Verify IP Address
- Instructions:
- ipconfig
- Notes:
- In my case, my IP Address is 192.168.1.106.
- In your case, your IP Address will probably be different.
| Section 4. Install Spybot Search and Destroy |
- Open Internet Explorer
- Instructions:
- Click the Start Button
- Type "Internet Explorer" in the search box
- Click on Internet Explorer
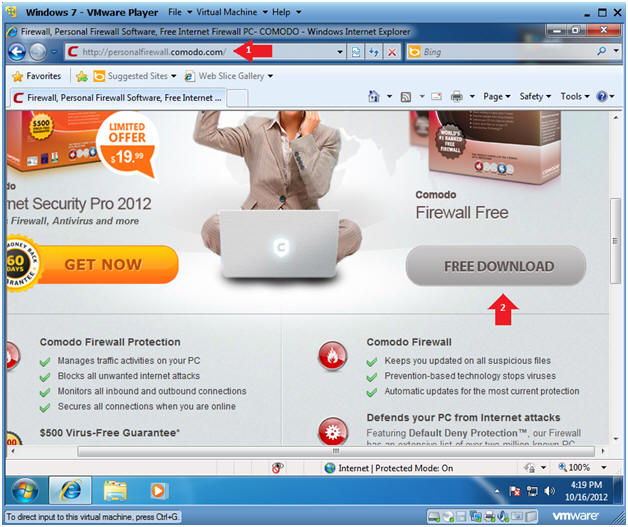
- Go to the Comodo Firewall Site
- Instructions:
- Paste the following website address in the URI box.
- http://personalfirewall.comodo.com/
- Click the Download Button
- File Download
- Instructions:
- Click Run
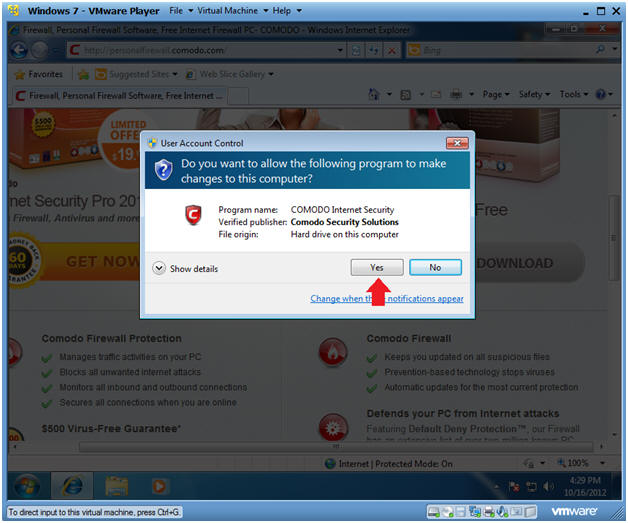
- Do you want to run this software?
- Instructions:
- Click Run
- User Account Control
- Select Setup Language
- Instructions:
- Select the language: English (United States) - By COMODO
- Click OK
- Optional Entry
- Instructions:
- It is not necessary to supply your email.
- It is not necessary to check any of the check boxes.
- Just click on Agree and Install

- Installing
- Informational:
- Continue to Next Step

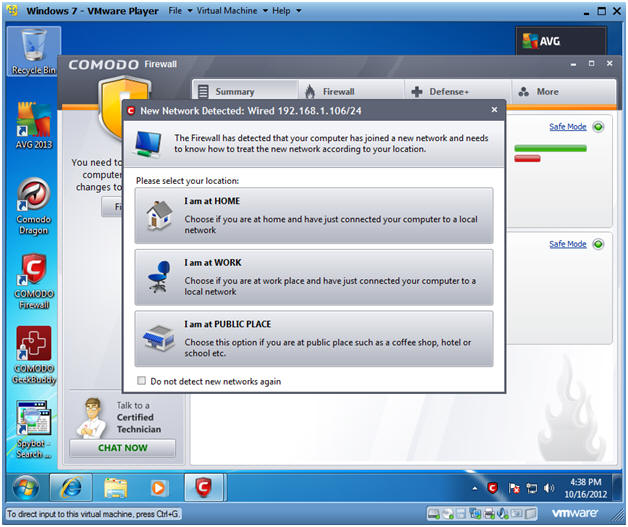
- Select Network
- Instructions:
- Select the appropriate network that matches yours.
- If you are at a school, coffee shop, airport, etc; then you will select "I am at PUBLIC PLACE"
- Restart Your Machine
- Instructions:
- Click Fix It
- Select Start Menu Folder
| Section 5. Configure BackTrack Virtual Machine Settings |
- Open Your VMware Player
- Instructions:
- On Your Host Computer, Go To
- Start --> All Program --> VMWare --> VMWare Player
- Edit BackTrack Virtual Machine Settings
- Instructions:
- Highlight BackTrack5R1
- Click Edit virtual machine settings
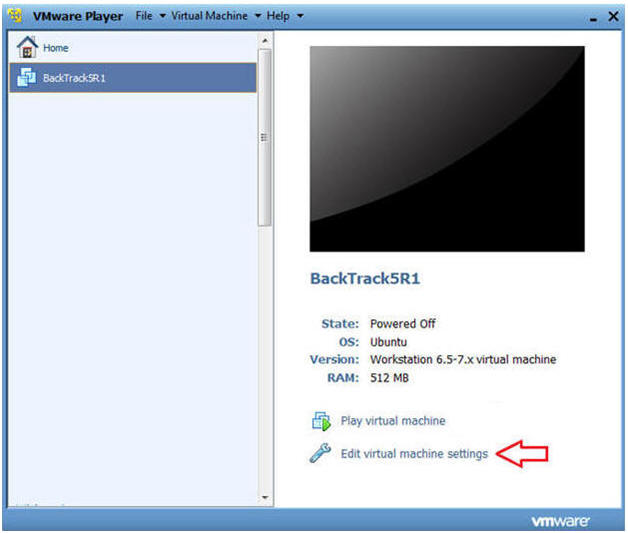
- Edit Network Adapter
- Instructions:
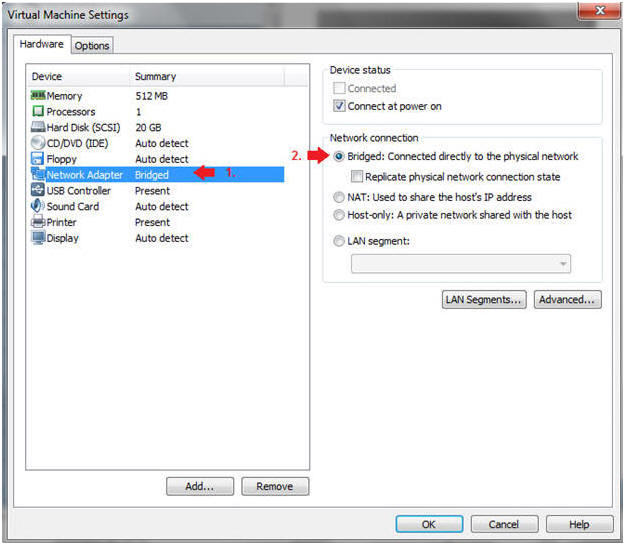
- Highlight Network Adapter
- Select Bridged
- Do not Click on the OK Button.
| Section 6. Login to BackTrack |
- Start BackTrack VM Instance
- Instructions:
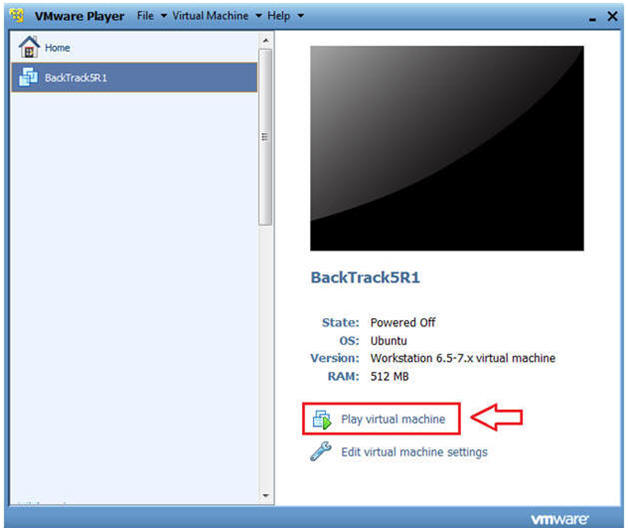
- Start Up VMWare Player
- Select BackTrack5R1
- Play virtual machine
- Login to BackTrack
- Instructions:
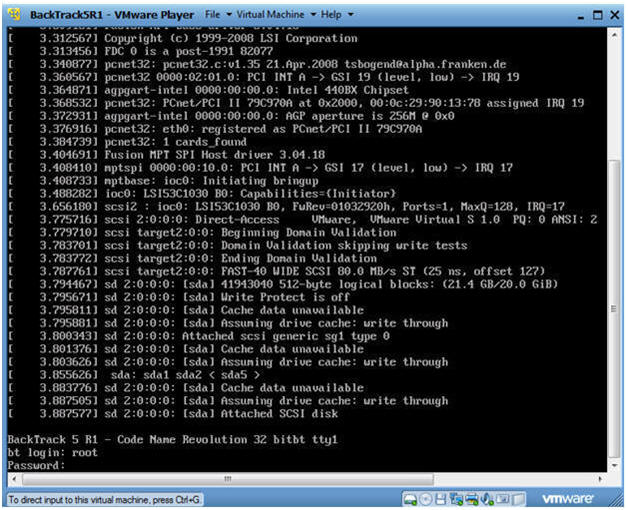
- Login: root
- Password: toor or <whatever you changed it to>.
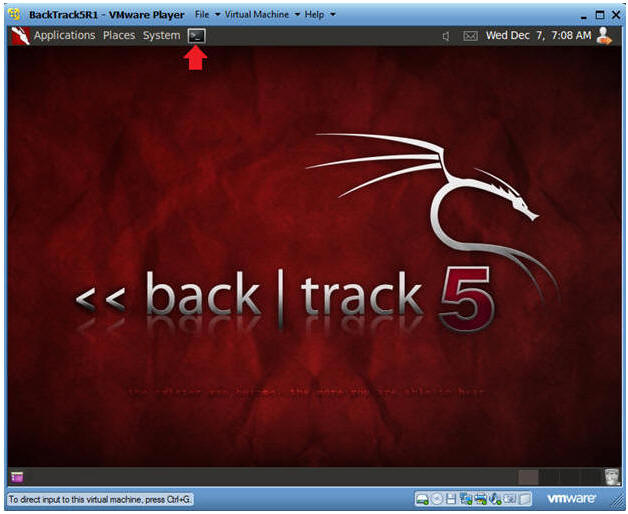
- Bring up the GNOME
- Instructions:
- Type startx
| Section 7. Open Console Terminal and Retrieve IP Address |
- Open a console terminal
- Instructions:
- Click on the console terminal
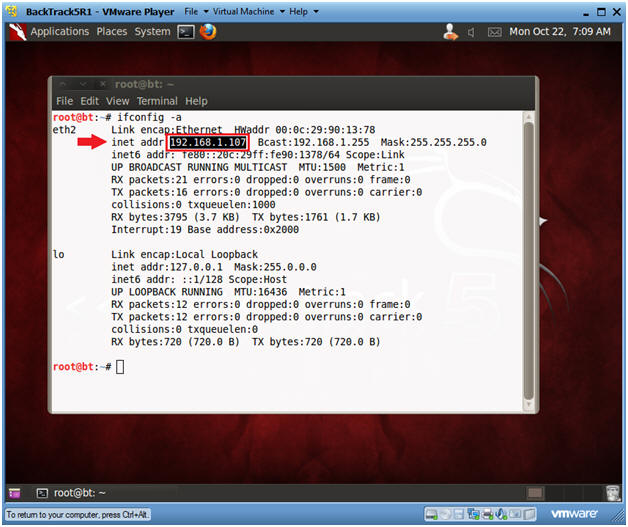
- Get IP Address
- Instructions:
- ifconfig -a
- Notes:
- As indicated below, my IP address is 192.168.1.107.
- Please record your IP address.
| Section 8. Test Comodo Firewall with BackTrack (Ping) |
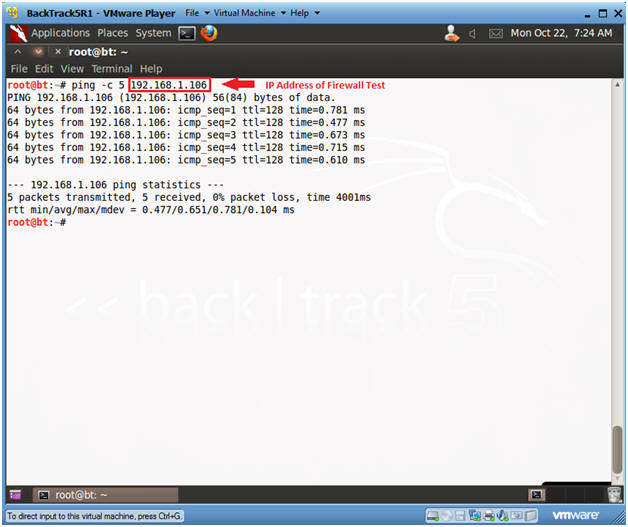
- Ping Windows 7
- Notes:
- Obtain the IP Address of the Window 7 machine running Comodo from (Section 3, Step 2)
- Instructions:
- ping -c 5 192.168.1.106
- -c, this flag indicates the number of pings, which in this example is 5 pings.
- 192.168.1.106 is the IP Address for my Windows 7 machine.
- Open Comodo Firewall
- Instructions:
- Click on the Comodo Firewall Icon
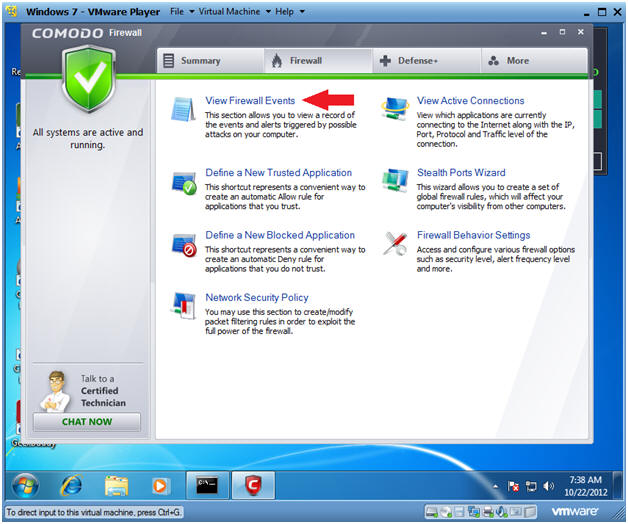
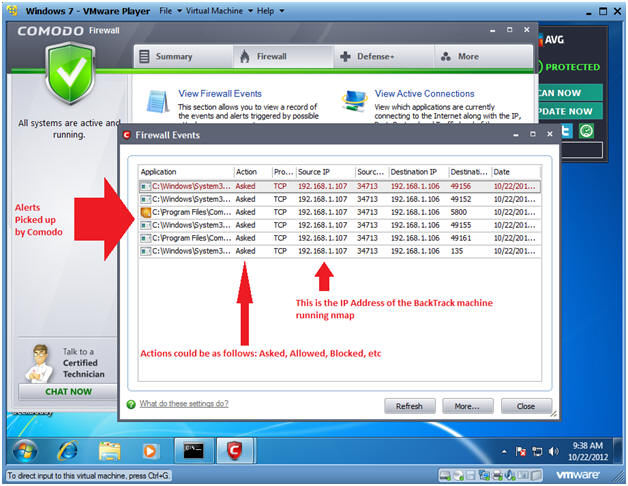
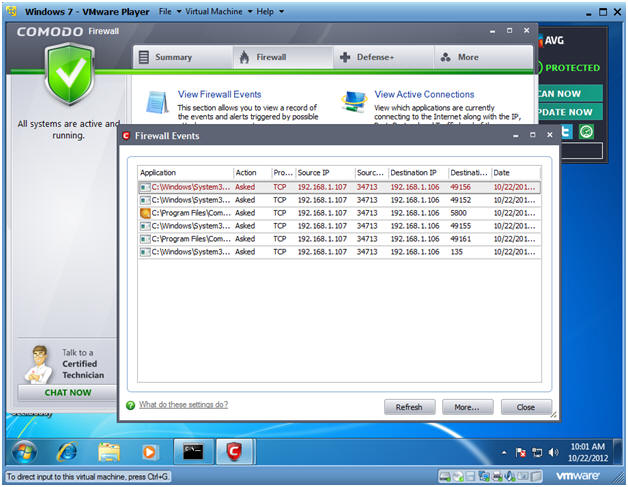
- View Firewall Events
- Instructions:
- Click on View Firewall Events
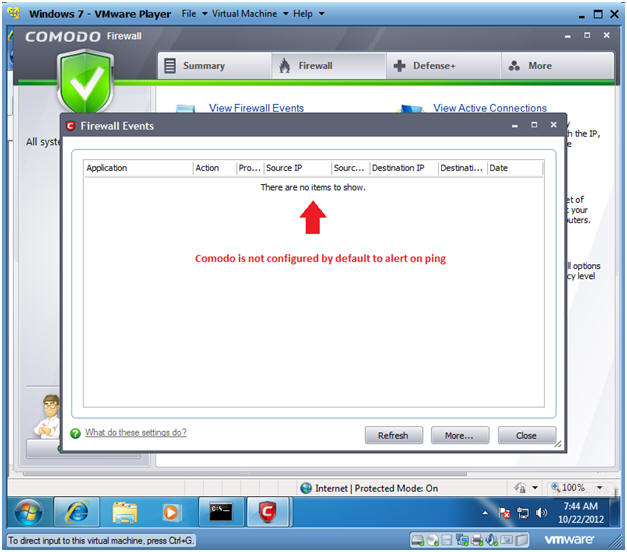
- Reviewing Firewall Events
- Note:
- Notice that Comodo did not alert us of the BackTrack ping.
| Section 9. Test Comodo Firewall with BackTrack (nmap basic scan) |
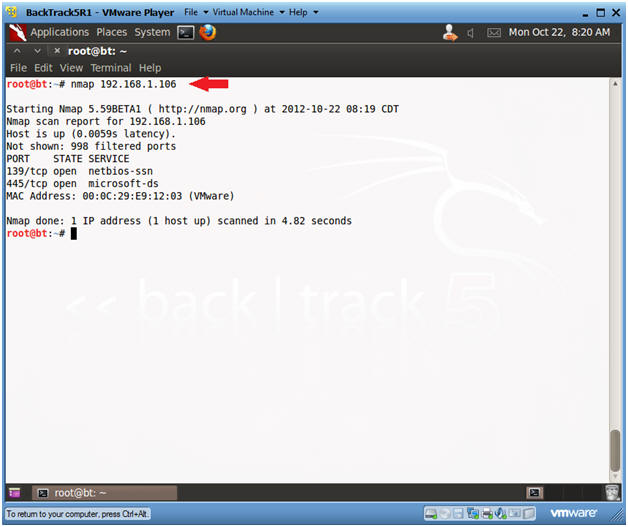
- Conduct Basic nmap scan
- Instructions:
- nmap 192.168.1.106
- Notes:
- Obtain the IP Address of the Window 7 machine running Comodo from (Section 3, Step 2)
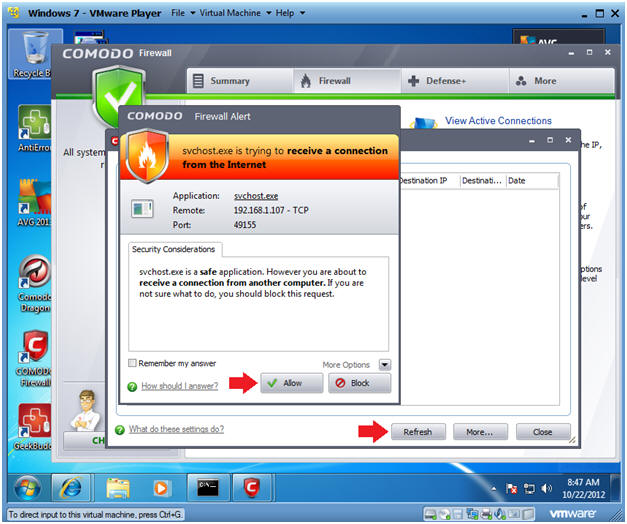
- Viewing Firewall Alerts
- Notes:
- Notice Comodo Firewall provides an Alert this time.
- Instructions:
- For our testing purposes, keep clicking the allow button until the alert messages stop.
- Click the Refresh Button.
- Viewing Firewall Alerts
- Notes:
- You should start seeing events that were initiated from BackTrack's nmap.
- Instructions:
- Continue to Next Section
| Section 10. Test Comodo Firewall with BackTrack (nmap TCP half-open stealth scan) |
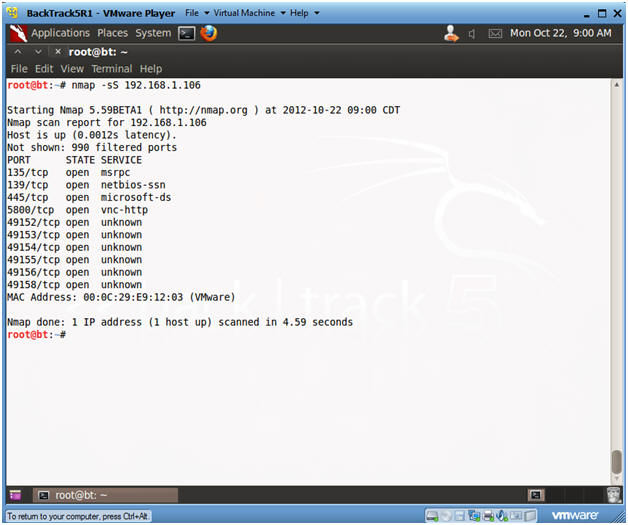
- Conduct nmap TCP half-open stealth scan
- Instructions:
- nmap -sS 192.168.1.106
- Notes:
- Obtain the IP Address of the Window 7 machine running Comodo from (Section 3, Step 2).
- -sS, This technique is often referred to as half-open scanning, because you don't open a full TCP connection. You send a SYN packet, as if you are going to open a real connection and then wait for a response. It is also relatively unobtrusive and stealthy since it never completes a TCP connections.
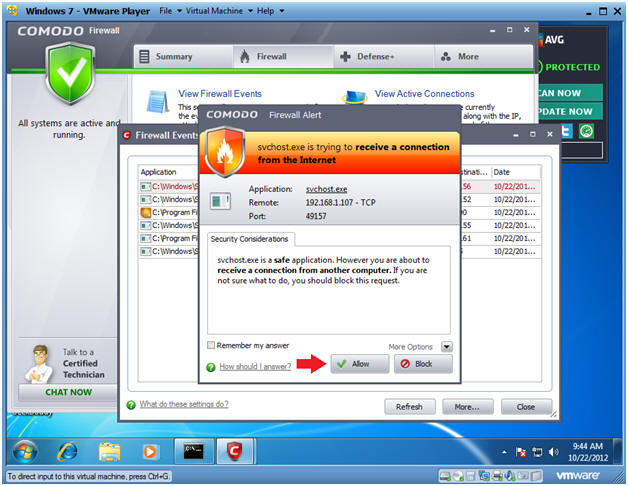
- Viewing Comodo Results
- Instructions:
- Click the allow button until no more alerts are displayed.
- Notes:
- Notice you were still alerted when nmap uses a half-open TCP scan.
| Section 11. Test Comodo Firewall with BackTrack (nmap SCTP INIT scan) |
- Conduct nmap SCTP INIT scan
- Instructions:
- nmap -sY 192.168.1.106
- Replace 192.168.1.106 with the Windows 7 IP Address obtain from (Section 3, Step 2).
- Notes:
- This technique is often referred to as half-open scanning, because you don't open a full SCTP association. You send an INIT chunk, as if you are going to open a real association and then wait for a response.
- SCTP is a relatively new alternative to the TCP and UDP protocols, combining most characteristics of TCP and UDP, and also adding new features like multi-homing and multi-streaming. SCTP INIT scan is the SCTP equivalent of a TCP SYN scan. It can be performed quickly, scanning thousands of ports per second on a fast network not hampered by restrictive firewalls. Like SYN scan, INIT scan is relatively unobtrusive and stealthy, since it never completes SCTP associations.
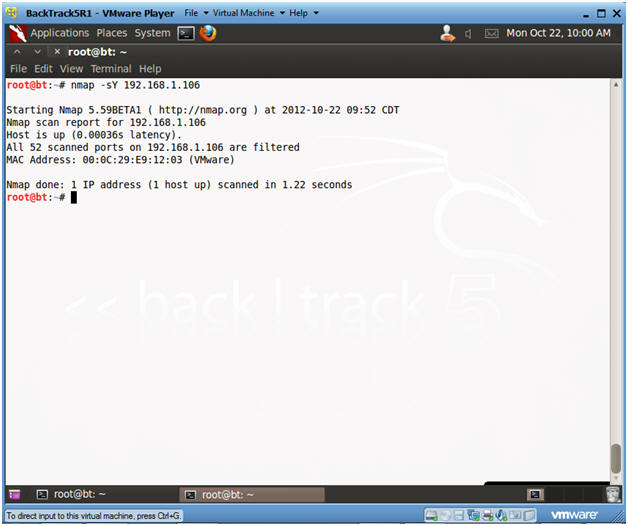
- Viewing Comodo Results
- Notes:
- Notice Comodo did not detect the half-open SCTP INIT scan.
- Instructions:
- Continue to Next Section
| Section 12. Test Comodo Firewall with BackTrack (nmap intense scan) |
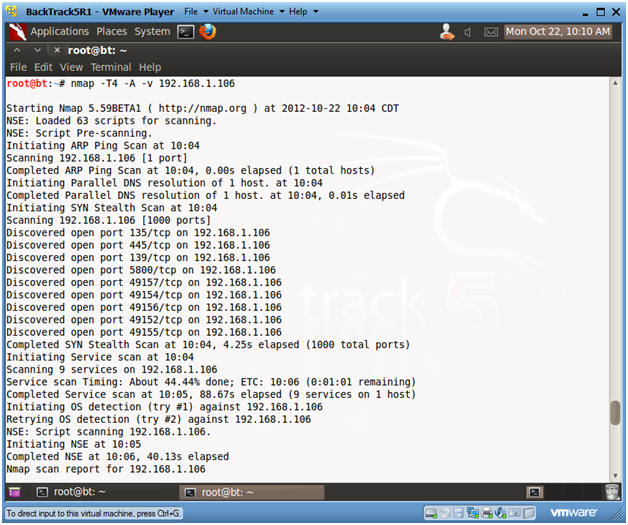
- Conduct nmap intense scan
- Instructions:
- nmap -T4 -A -v 192.168.1.106
- Replace 192.168.1.106 with the Windows 7 IP Address obtain from (Section 3, Step 2).
- Notes:
- -T, is a timing template with the following settings: paranoid (0), sneaky (1), polite (2), normal (3), aggressive (4), and insane (5). The first two are for IDS evasion.
- -A, to enable OS and version detection, script scanning, and traceroute.
- -v, is verbose mode.
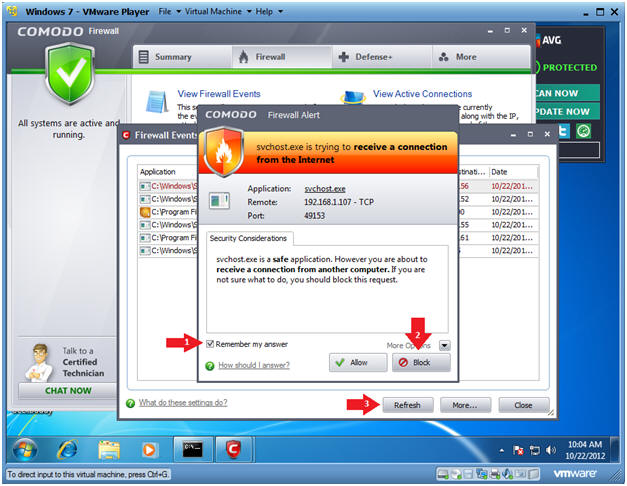
- Viewing Comodo Results
- Notes:
- Notice Comodo is now going crazy.
- Instructions:
- Click Remember my answer
- Keep clicking on the Block button as Alerts appear.
- Click the Refresh button
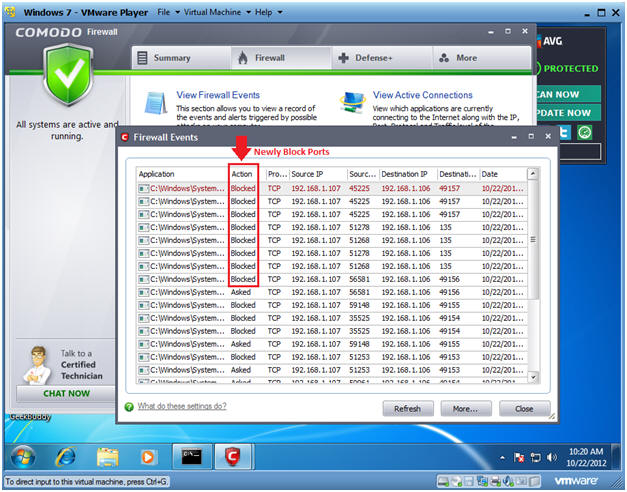
- Analyzing Comodo Results
- Notes:
- Notice Comodo is now Blocking scans from 192.168.1.107 for ports 49157, 135, and 49156.
- Instructions:
- Continue to Next Step.
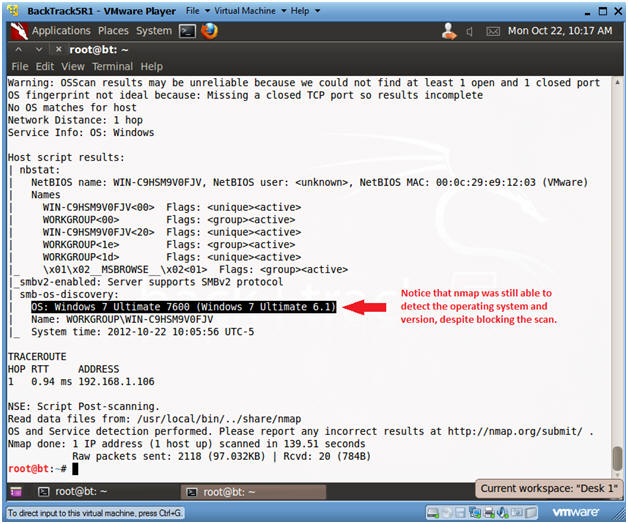
- Analyzing nmap Results
- Notes:
- Notice that although you blocked the intense scan with Comodo, nmap was still able to determine the operating system and version.
- Instructions:
- Continue Next Section
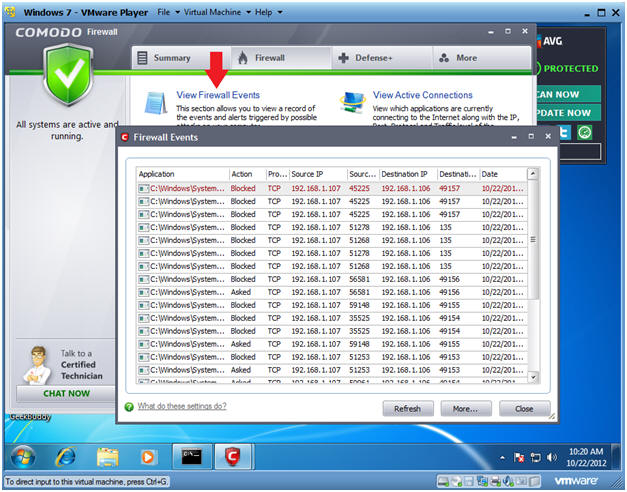
- View Firewall Events
- Instructions:
- If the Comodo Firewall Dashboard is not open, click on the Comodo Firewall desktop icon.
- Once opened, Click on View Firewall Events.
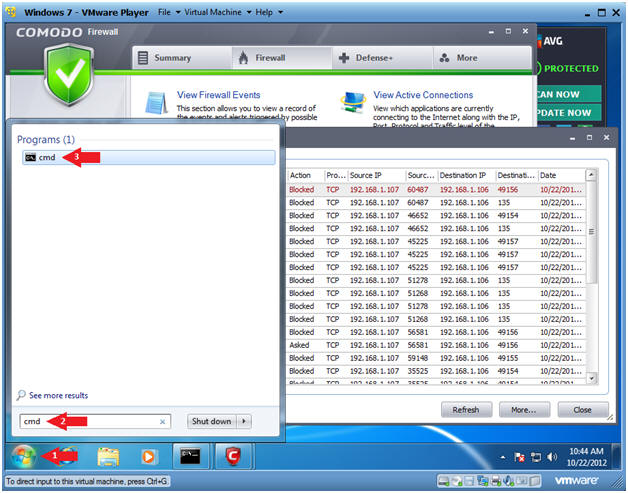
- Open a Command Prompt
- Instructions:
- Click the Start Button
- Type cmd in the search box
- Click on cmd
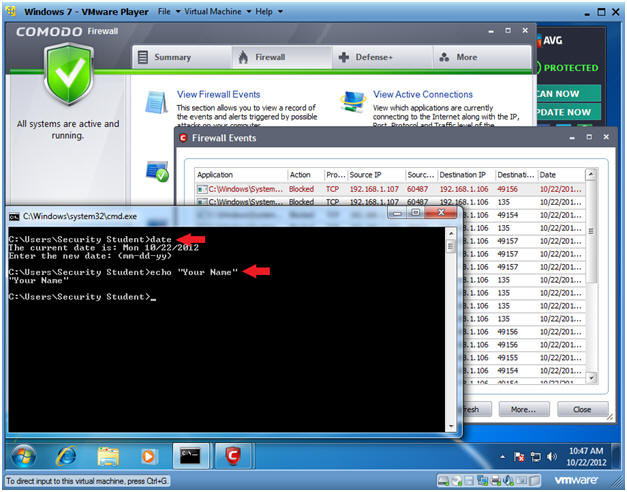
- Proof of Lab Instructions
- Instructions:
- date
- Press <Enter>
- echo "Your Name"
- Replace the string "Your Name" with your actual name.
- e.g., echo "John Gray"
- Do a PrtScn
- Paste into a word document
- Upload to website www.antoanthongtin.edu.vn
-






































0 nhận xét:
Đăng nhận xét